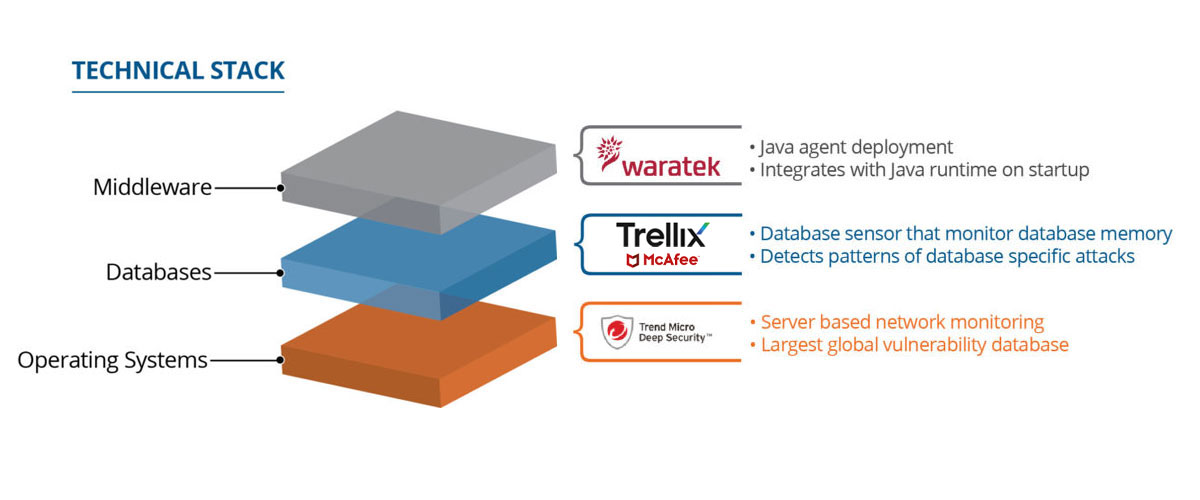
Comprehensive Risk Mitigation
Our extensive security strategy offers a blanket of protection across applications, middleware, databases, and operating systems to prevent and combat potential threats. Our security experts’ partner with your team to provide recommendations on strengthening your protection and improving compliance across your system’s infrastructure.
- Discover & Harden
- Incident Response
- Threat Intelligence
-
Security Assessments
We identify weaknesses and opportunities to improve the security of your systems by providing guidance on hardening techniques and configuration adjustments
-
Audit Compliance
We work with your audit teams to help you adjust your controls to stay compliant under a third-party support model
-
Vulnerability Management
Our security staff is standing by to resolve your vulnerability concerns, even your customizations
-
Security Tooling
We offer a suite of security products to complement your existing security and allow it to adjust to a third-party support model.
-
Security Bulletins
We continually evaluate OEM security issues and publish regular bulletins describing product vulnerabilities and best practices for improving hardening standards and mitigating these vulnerabilities.
Vendor Patching | Vulnerability Management | |
|---|---|---|
| TIMING | Patches are delayed and can take months or even years for a final resolution. | Compensating controls and configuration suggestions are relayed to the customer within days to weeks. |
| SPECIFICITY | Generic patches can be problematic to customizations. | Receive patches and solutions tailored to your system. |
| VERSIONS | Patches may not be available for older versions and applications. | By addressing issues at the infrastructure level, you protect the entire stack, regardless of the app versions. |
| TESTING | Patches require valuable time to test and install. | We isolate testing to the area affected by the vulnerability rather than the entire system. |
| APPLICATION | Organizations lack the staff or patch system to regularly apply patches. | Address the issue at the source and convey the proper hardening techniques. |