Cybersecurity should be a top priority for every company, to stop threat actors from exploiting vulnerabilities in your systems – which can lead to data breaches, financial loss, and reputational damage.
But securing your systems isn’t a one-and-done operation, as new threats are constantly emerging. The US National Institute of Standards and Technology (NIST) vulnerability database recorded a staggering 51,665 vulnerabilities between 2020 and 2022, an average of two per hour.
This article has everything you need to understand and successfully implement an effective vulnerability management lifecycle strategy.
What is the vulnerability management lifecycle?
The vulnerability management lifecycle is a continuous, proactive process used to identify and mitigate security risks in IT systems. Because the cyber threat landscape is always changing, the process has to be ongoing for it to be effective.
Rather than pursuing the unrealistic goal of eradicating all threats, the vulnerability management lifecycle takes a more practical approach. It aims to categorize the severity of risks, so the most serious vulnerabilities can be addressed as quickly as possible with the available resources.
What are the 5 stages of the vulnerability management lifecycle?
The vulnerability management lifecycle consists of five stages ongoing stages:
Stage 1: Discovery
Start by creating an inventory of all assets in your IT system so you know the potential attack surface to scan for vulnerabilities.
The types of assets that make up IT systems include:
- Endpoints: These are the physical devices that connect to your networks, from IoT devices to workstations. They’re common points of entry for malicious actors, so they should be one of the first stops for vulnerability scans.
- Servers: Identify both physical and virtual servers during discovery. As the backbone of your network, compromising these critical assets would pose a serious risk to your entire company.
- Network devices: These include firewalls, switches, bridges, modems, and routers. These assets provide the infrastructure on which your network functions.
- Applications: This should cover all non-hardware tools that your company works with. Whether it’s something used for database management, DevOps, issue tracking, or communication, it needs to be included.
- Operating systems: The scope of your software evaluation should cover not merely apps, but also your software infrastructure.
- Data: Collect information across as many areas as you have, including metrics, logs, and trace data. Analyzing trends in the data could provide insights and reveal anomalies.
- Dependencies: This involves mapping out the entire system to see relationships between physical and digital assets. This way, you understand the ripple effect from potential issues and you can decide where to focus on the most.
Stage 2: Prioritization
As we mentioned at the start of this article, the vulnerability management process is about deciding which threats pose the most serious risk and working through them first.
The second phase of the lifecycle is where you prioritize issues by ranking the value of assets and the seriousness of vulnerabilities. The factors you’ll have to consider when making these choices are:
- Threat intelligence rating.
- Importance of the affected asset.
- Likelihood of exploitation.
- Potential threat if exploited.
By the time you’re done with discovery, you should have enough information about your assets to make these considerations. According to the NIST vulnerability database, medium-level threats are the most common, followed by high, then low.
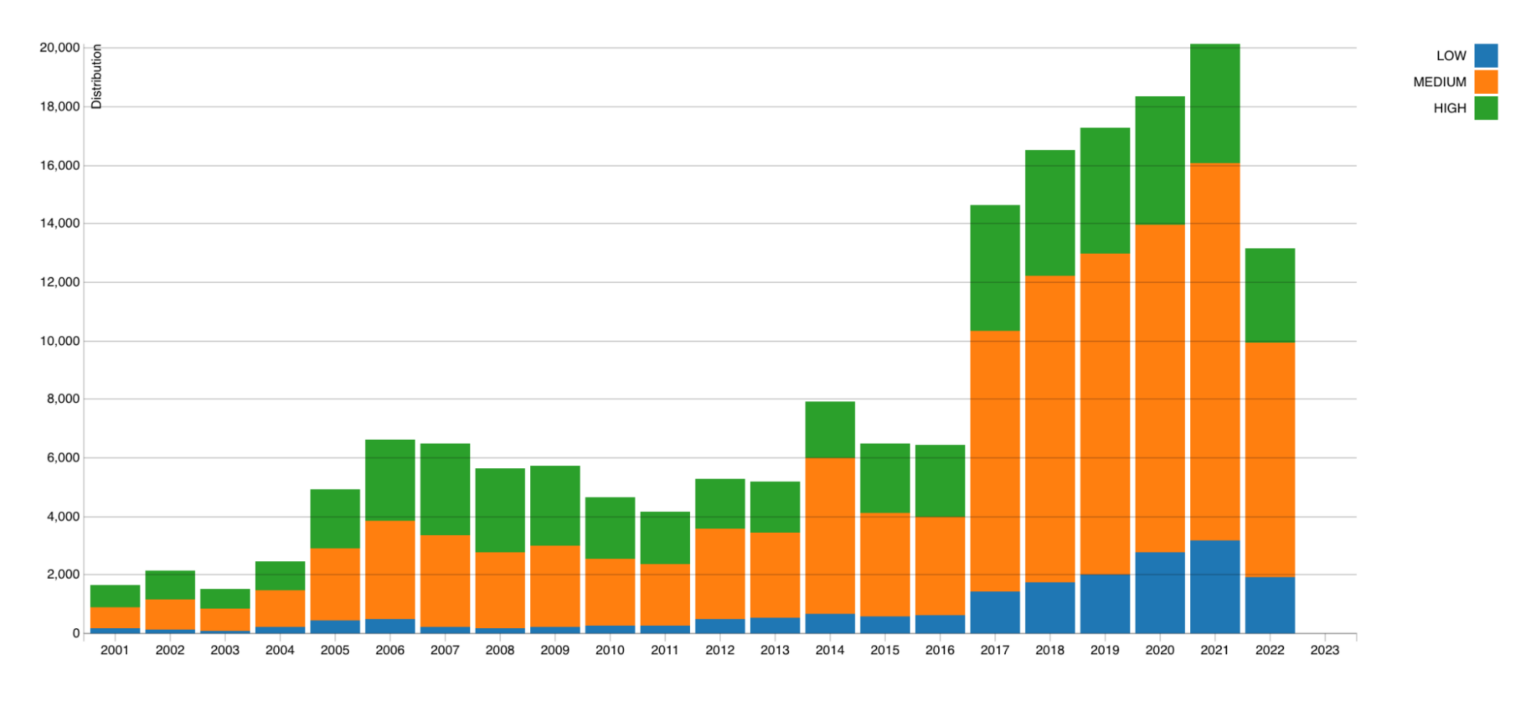
Deciding which risks to prioritize and which you can safely hold off on addressing is a delicate balancing act. With limited resources, amid an ever-evolving threat landscape, you must attempt to triage the vulnerabilities that are most important now.
Things could fall apart at this stage if you don’t have the right level of expertise on your side. Luckily, Spinnaker Support has a team of cybersecurity experts that can handle the tricky challenges of sorting vulnerabilities by severity.
Stage 3: Resolution and mitigation
After identifying the most serious vulnerabilities, it’s time to start managing them.
Once again, the name of the game here is efficiency. You might come across a threat that you can’t eliminate immediately. Trying to eliminate it could slow you down and divert your attention from emergent threats. Instead, you should find another way to mitigate it, e.g. by moving it into containment to dampen its potential impact and lower the threat level.
For some vulnerabilities, you might think it’s best to wait for a patch from the software publisher, but this isn’t an ideal strategy. What’s serious to your business might be trivial to the majority of the vendor’s customer base, so they’re not always incentivized to move quickly.
A strong alternative would be to enlist expert third-party support, where a proactive approach to security eliminates the need to wait around for vendor updates. This is especially true if your vendor discontinues support for a legacy product that you still rely on. Spinnaker Support can keep your systems running – securely – for as long as you need it.
Stage 4: Verification and monitoring
After you’ve addressed the vulnerabilities, you’ll need to audit your system to verify the effectiveness of your remediation efforts. Penetration testing is a good practice to include at this stage of the lifecycle.
Run continuous monitoring on your systems to see how they respond to the changes, and be sure to check any relevant dependencies to ensure you didn’t inadvertently break anything.
Stage 5: Reporting and improvement
Document your findings and evaluate your performance. Some key metrics and KPIs you could assess here include:
- Time to detect: The mean time to detect (MTTD) shows how quickly you were able to identify vulnerabilities.
- Time to action: The average time to action shows how fast your team was able to respond to the threats after identifying them.
- Time to remediation: This tracks the time it took the security team to resolve an issue.
- Risk age: The longer a vulnerability was in the system, the more impact it could have.
- Risk score: This is a measure of how exposed a company’s security is, with a risk profile based on factors like password strength and level of encryption.
- Asset coverage: This scores your asset inventories by the average number of vulnerabilities per asset.
- Total risk remediated: Measure what portion of the issues detected were successfully addressed.
This step of the lifecycle gives you the insights you need to refine data security practices and vulnerability management as you start the process again.
Best practices for implementing the vulnerability management lifecycle
The vulnerability management lifecycle should be a part of your company for as long as you’re in business. Here are some tips to set yourself up for success:
1. Break up each stage into chunks
Effective vulnerability management calls for agility.
One way to introduce this into the lifecycle is by breaking each step down further into manageable chunks. Because it’s a continuous process, you can tackle the entire lifecycle with sprints that maintain your momentum.
2. Automate your security testing
Because the vulnerability management lifecycle is continuous, it’s possible to map the fundamentals of DevSecOps onto it.
DevSecOps is like DevOps, the methodology that allows software development teams to move at speed by leveraging automation, but with a higher emphasis on security.
One of the main pillars of DevSecOps is the automation of security testing. It works by simulating attacks against the system to identify vulnerabilities.
A team of security professionals will almost certainly struggle to perform enough of these kinds of tests manually, even at a small scale. By automating it, they’re able to catch vulnerabilities early and at scale, and they free up enough time to focus on other areas of security.
Automation also reduces the potential impact of human error, which, as we’ll discuss below, poses a significant threat to cybersecurity.
3. Develop a regular schedule
We recommend creating regular scan schedules for vulnerability assessments. Ideally, these scans would also be automated to account for human error and availability.
As we mentioned above, it’s possible to manage the vulnerability management lifecycle with sprints. This would involve setting the parts of the process that involve humans to take place within a specific timeline. To stay agile, we recommend keeping each full cycle to a month at the longest.
4. Train your team
The human element is the weakest part of any security system, and it’s present in 74% of incidents. The best way to mitigate this risk is by providing your entire team with cybersecurity awareness education.
5. Partner with a third-party support provider
A third-party support provider like Spinnaker Support is an ideal middle ground between relying on the publisher for patches and building an in-house vulnerability management team from scratch.
Spinnaker Support provides a team of Level 2 and 3 engineers for all managed services. There are also Level 4 engineers, who have an average of 20 years of experience, for third-party support services. Their response time is under 15 minutes and they’re available 24/7/365.

With Spinnaker Shield, you get a proactive and continuous vulnerability management solution. It’s available for products from major vendors like Oracle and SAP.
Aside from vulnerability management, here’s what you get with Spinnaker Shield:
- Security assessments: We walk you through how to assess your systems for security flaws and what you can do to manage them.
- Audit compliance: We help you configure your systems so you end up with a functional setup that complies with your licensing agreements and relevant laws.
- Customized security support: We provide security advice tailored to your unique needs and concerns.
- Full-stack security tooling: For clients who switch to third-party support, we provide support for all the security tools you have in your system so they don’t turn into a liability.
- Security bulletins: We investigate and report on vulnerabilities present in various products and services. These reports also include information on how to deal with these security issues.
Shield your digital assets with Spinnaker Support
The vulnerability management lifecycle is a continuous process of threat identification and mitigation for every asset within a company’s IT infrastructure, prioritized by severity. This imposing task requires proactive engagement – it’s not enough to simply sit back and await vendor patches.
Vulnerability management programs call for the kind of expertise that’s only developed from a decades-long background in cybersecurity.
Spinnaker Support, through its Spinnaker Shield service, provides expert vulnerability management and third-party support services for world-class security. With this model, enterprise clients tackle threats proactively and don’t rely on software publishers for security patches.
Contact us today when you’re ready to take charge of your company’s security.


