Eighty-seven percent of all global commerce, equal to about $46 trillion, comes from SAP customers. With a load-bearing system of this magnitude, security is of paramount importance.
SAP security monitoring helps ensure the vendor’s products and services remain available and uncompromised. If you’re a SAP customer yourself, you understand how these needs impact your organization, from threat detection to access control.
This article will outline the key components of SAP security monitoring so you can strengthen your defenses with effective strategies.
What is SAP security monitoring?
Security monitoring is the continuous process of detecting and managing vulnerabilities in IT systems.
In SAP systems, this process spans three main areas:
- Access control, involving user authentication, authorization, and privileges.
- Data security, involving data backups to prevent threats like data loss and ransomware.
- Application security on websites, web applications, and similar platforms.
SAP security provides users with a collection of tools for security monitoring, including:
- Enterprise Threat Detection, which pinpoints issues and helps teams address them.
- Focused Run, which monitors systems, issues alerts for threats, and supports analytics and diagnostics.
- EarlyWatch Alert, an automated monitor that scans the administrative areas of SAP systems for threats.
- Code Vulnerability Analyzer, used to scour business applications for vulnerable code.
Unfortunately, while this suite of tools is a good start, it’s not enough to combat the sheer magnitude of emerging cyber threats today.
What types of threats exist for SAP systems?
SAP’s patch notes revealed the most serious weaknesses and vulnerabilities in its systems related to:
- Code injection: The attackers introduce malicious code into the system for the application to execute. Some instances of this involved SQL injection, where the attack targets the database.
- Authorization and authentication-based attacks: These include access control and privilege escalation, where attackers attempt to gain control of the system by pretending to be authorized users. They also cover verb tampering attacks, where attackers change the actions executed when certain parts of a program run.
- Cross-site scripting (XSS): Attackers inject malicious code into trusted but vulnerable websites. This approach gets around same-origin security policies that isolate different websites. This type of vulnerability also shows up in SAP systems as improper neutralization of input.
- Request forgery: The most common attack type under this category was server-side request forgery (SSRF). In this approach, attackers send requests from the server to other areas of the system to gain access to them.
While these are vulnerabilities that SAP caught and patched prior to reporting on them, the truth is they’re not always addressed before attackers exploit them. These same vulnerabilities often reappear in other areas of SAP systems.
Malicious actors take advantage of more than just the vulnerabilities mentioned above, which poses a significant risk to all SAP customers.
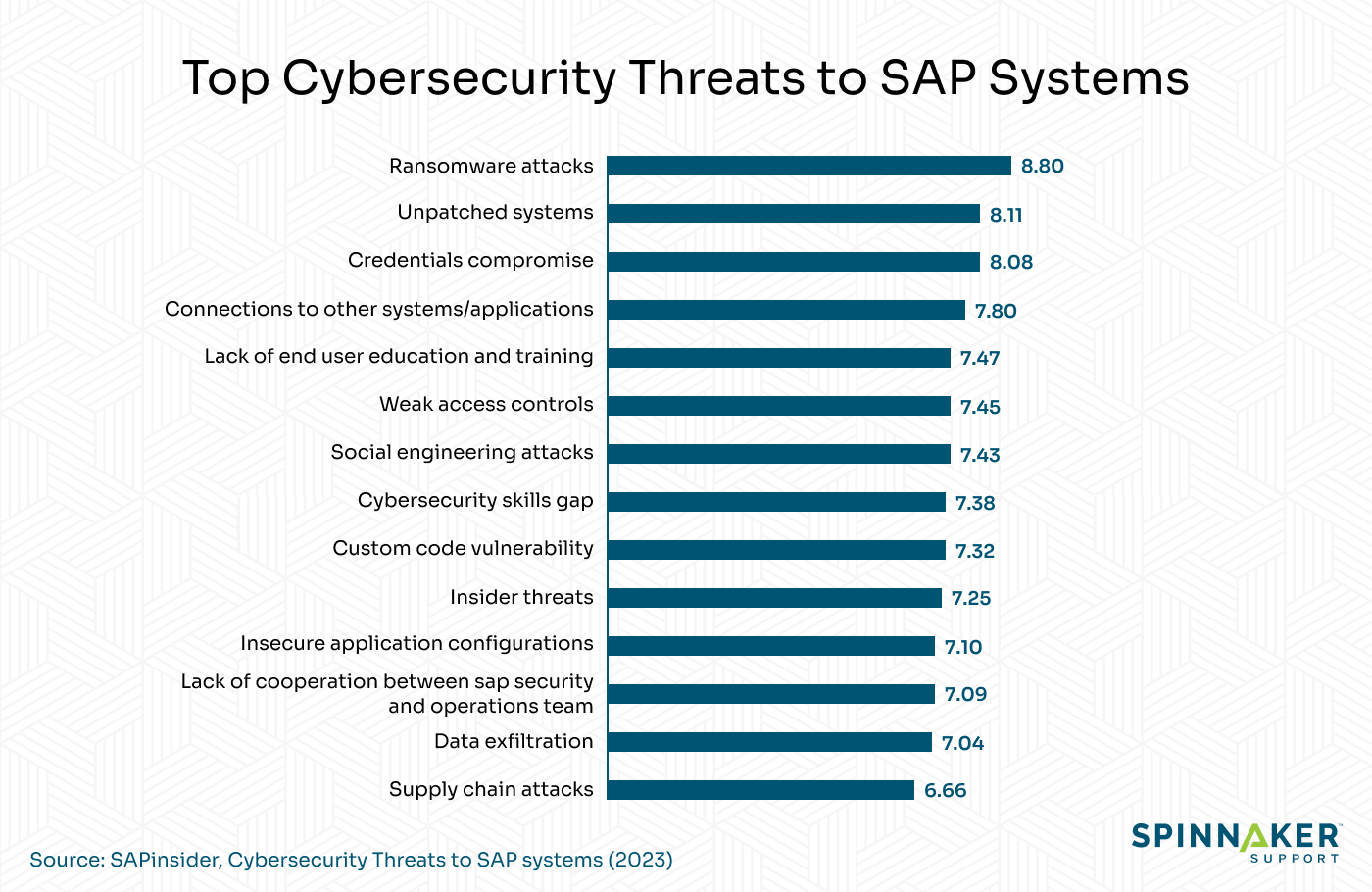
To give you the full picture, here are some of the biggest threats to SAP systems:
- Ransomware: This is the biggest threat to SAP systems, where attackers use whatever vulnerabilities they can to take over a company’s systems.
- Compromised credentials: Attackers gain access to an authorized user’s login information, usually their password, and use them to infiltrate a system.
- Connections to other systems and applications: These threats come from vulnerable systems connected to the SAP one, which attackers can use as a bridge.
- Poor user education: Team members, especially inexperienced ones and those outside the security team(s), aren’t trained on how to spot, report, and mitigate security threats.
- Weak access controls: This usually manifests as a lack of multi-level access controls in the system, especially two-factor authentication.
- Social engineering attacks: These range from honeytraps to phishing attacks, where attackers manipulate an unsuspecting user into letting them into the system.
- Cybersecurity skills gap: Security personnel might not be up to speed on the latest cybersecurity threats, making it easier for advanced attackers to best them.
- Custom code vulnerabilities: Any additional functionality grafted onto a system might introduce new vulnerabilities. Spinnaker Support’s Third-party support services extend to the customizations as well.
- Insider threats: These involve attacks carried out by a member of the company, such as espionage, sabotage, and data theft.
A third-party support partner like Spinnaker Support can help you manage most of these threats. Our experts take a proactive approach to strengthen and improve your security posture.
Why should SAP security monitoring be a priority for your company?
With the full scope of the threats facing your SAP systems, it’s time to start thinking about securing them.
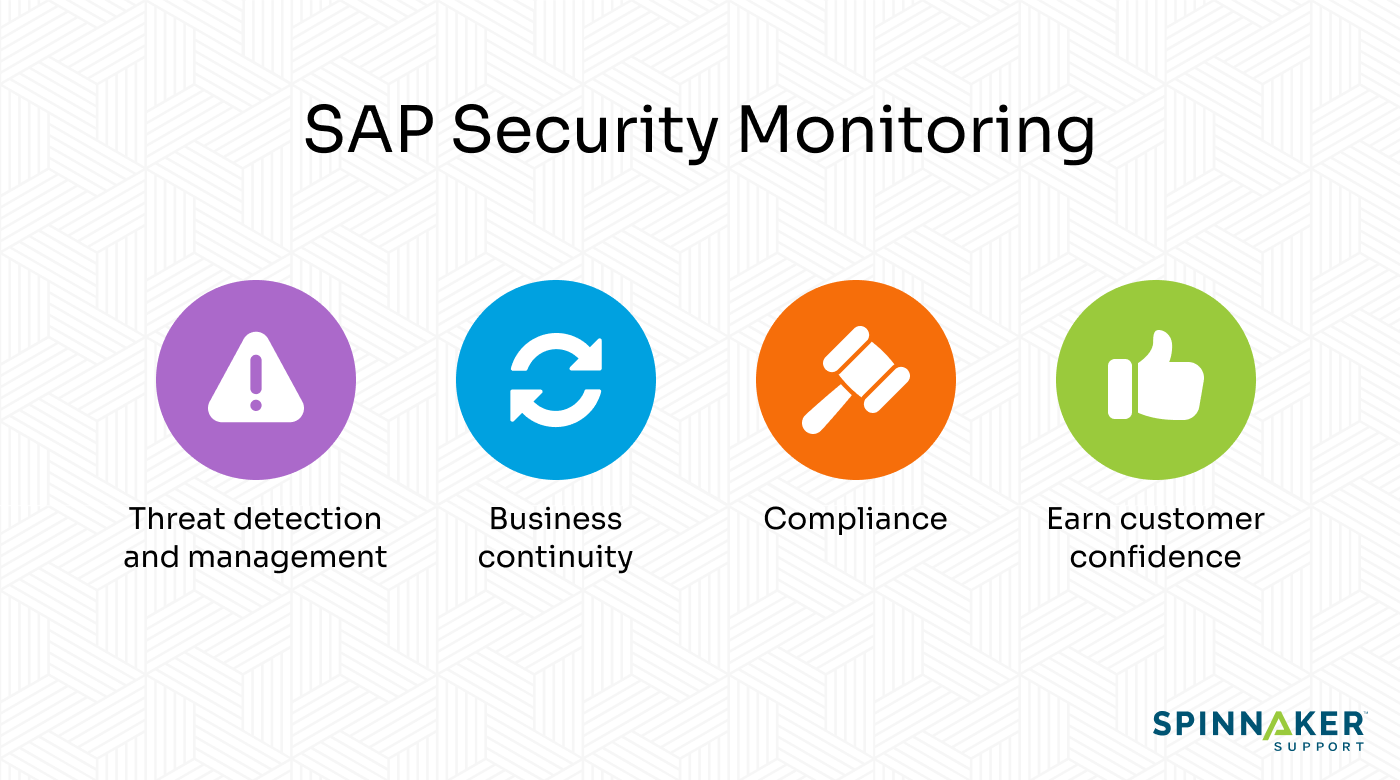
Here are the reasons why you shouldn’t wait to get started:
- Threat detection and management: Security monitoring identifies threats and lets you mitigate them before they develop into a catastrophe.
- Business continuity: You sidestep security incidents like ransomware so they don’t stop your business activities.
- Compliance: In some countries, maintaining cybersecurity is a regulatory requirement. Laws governing this include the US Health Insurance Portability and Accountability Act (HIPAA) and the EU GDPR.
- Earn customer confidence: When you can prove to your customers that their data is safe in your hands, they might be more likely to associate you with reliability and build loyalty with your brand over time.
Weak security monitoring practices can have disastrous consequences. One of the most well-known recent examples of this is the Equifax breach, which was the result of poor patch management. The ensuing class-action lawsuit ended in a $500 million settlement, and the company has since spent $1 billion to fortify its security systems.
How can you monitor your SAP applications for potential security risks?
The cost of a security incident might be more than your company can afford to shoulder. For this reason, the best strategy is a proactive one.
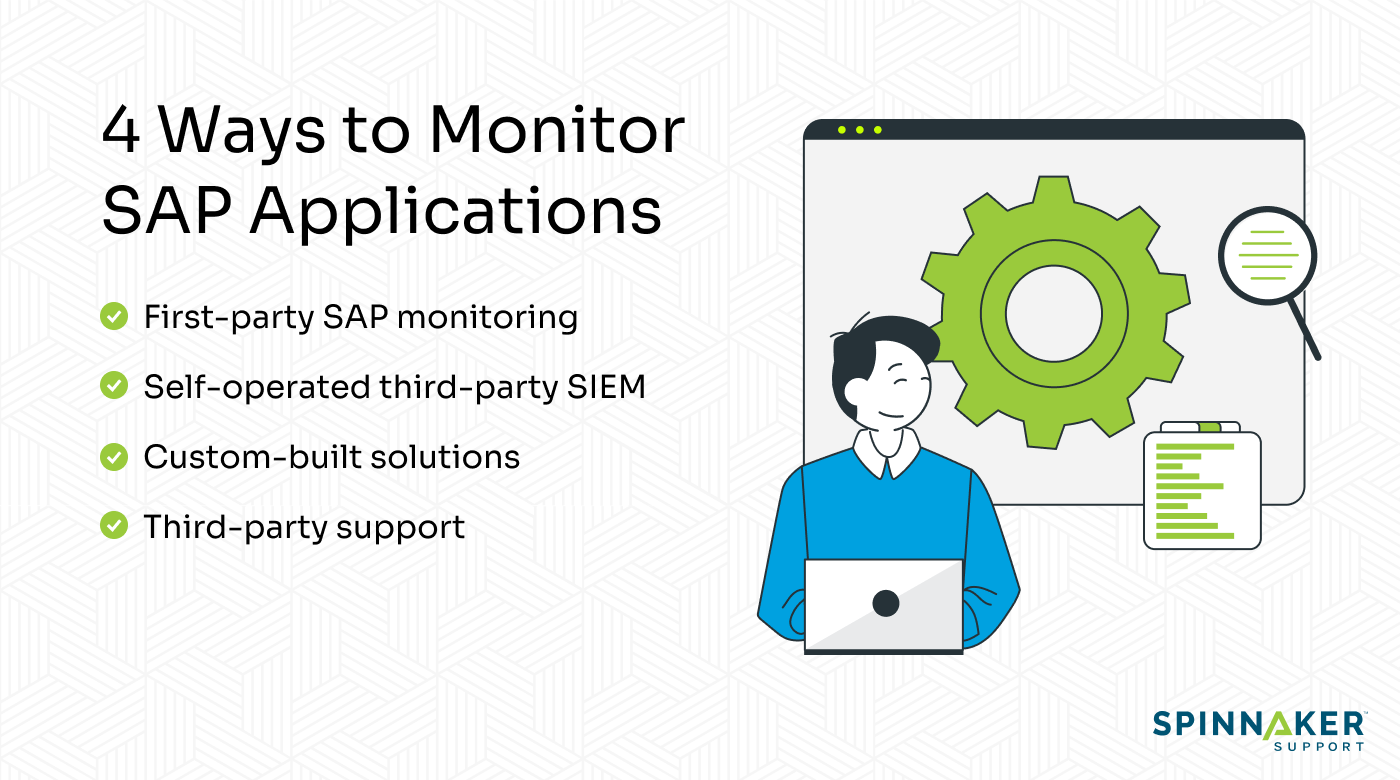
Here are four ways you can implement security monitoring in your organization.
1. First-party SAP monitoring
This approach involves leaving your security monitoring needs to the vendor. Some companies might have signed the SAP support contract because they believed it was the only option they had for security.
On the face of it, it looks like the most ideal way to go — the vendor should understand its product better than anyone. However, this isn’t always the case, and you might find yourself in a worse position security-wise if it’s the one you choose.
It’s in the best interests of a company like SAP, with its hundreds of thousands of customers, to prioritize vulnerabilities based on what poses the biggest risk to most of its clients.
If you’re vulnerable to a threat but you’re in the minority, your security patch might arrive when it’s too late.
2. Self-operated third-party SIEM
This involves using third-party security information and event management (SIEM) tools like IBM QRadar and Azure Sentinel, operated by an in-house team.
While it’s a step above first-party support in that you can shop around and pick one for yourself, these tools are often one-size-fits-all solutions. This means they might not be comprehensive enough to cover your unique and evolving security needs.
Like first-party support, updates also roll out depending on what’s most valuable to the provider’s business goals rather than yours.
Even if the tool is open-source like OSSEC or OpenSearch, you’ll still need personnel to manage it, and this introduces additional costs.
3. Custom-built solutions
You can also use proprietary tools to handle your SAP security monitoring needs, but in-house software is often resource-intensive.
Between the time and money investments, custom-built solutions might be more trouble than they’re worth. This might explain why businesses are moving away from them — only 45% of the software companies use is proprietary, and they expect it to reduce to 37% within the next two years.
Furthermore, while they might work as a replacement for your SAP workflows, security needs change too often for the one-and-done solution that is proprietary software. This arguably makes them the hardest solution to recommend for security.
4. Third-party support
Third-party support services from a company like Spinnaker Support allow you to offload the work of maintaining your SAP systems to a team of qualified professionals.
It’s better than first-party monitoring because it’s cheaper and you remain in charge of the system at large, especially if you’re running your SAP system in a private environment.
Additionally, the security team continuously monitors your systems and deploys timely patches tailored to your needs. This makes it a more agile solution than proprietary software.
Security monitoring best practices to follow for safer SAP systems
Whichever option you pick for security monitoring, here are some of the best practices you should implement for success.
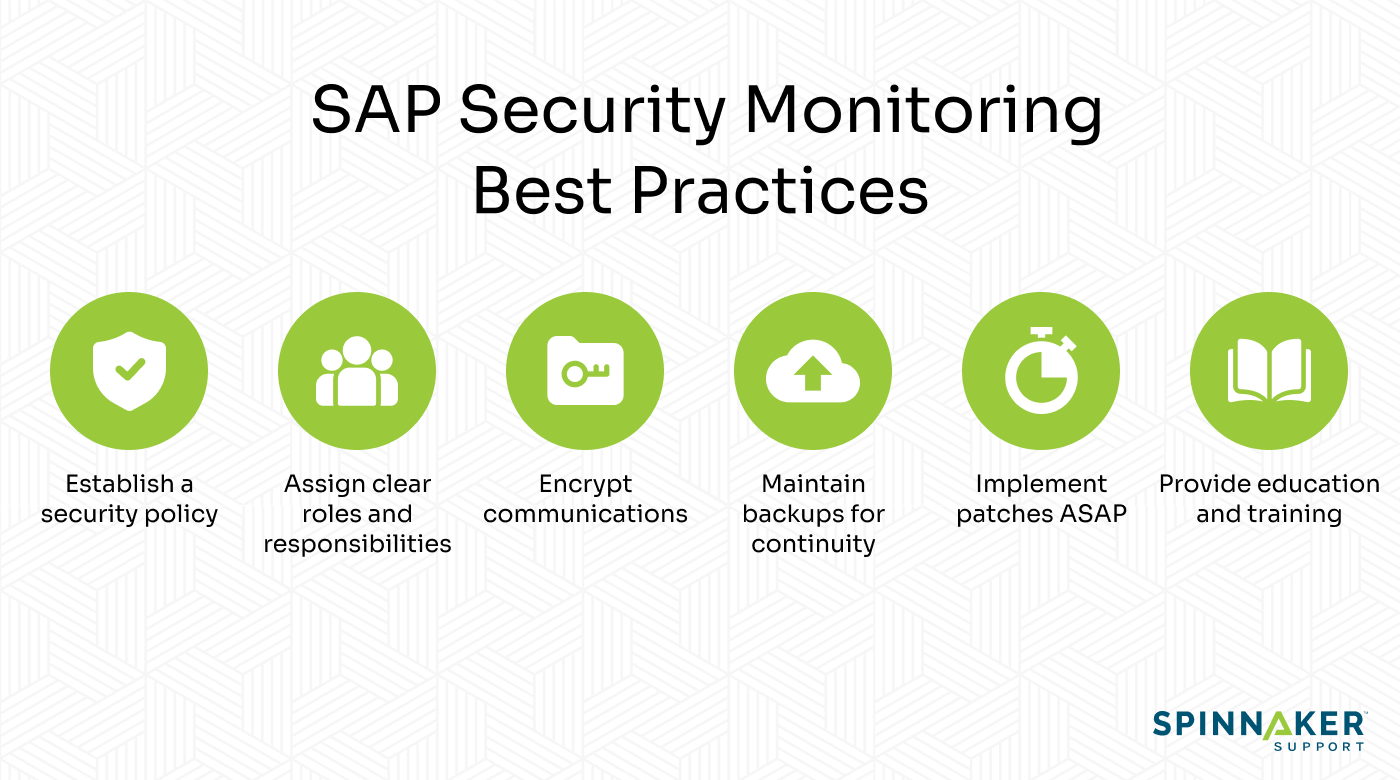
1. Establish a clear security policy
Develop a well-defined security policy that establishes guidelines for monitoring, logging, and responding to security incidents.
Identify all critical assets, including data, and determine the best ways to protect each one of them.
Implement continuous monitoring and determine how the policy handles logging — what logs are created, when, and how long they’re stored.
Incorporate regular security assessments into this policy. Evaluate the logs and any other data gathered from your systems to sniff out suspicious activity and vulnerabilities early on.
For example, the policy could require multi-factor authentication for access at all levels, including for the security team(s).
2. Assign clear roles and responsibilities
Designate roles and responsibilities to all stakeholders, including system administrators, security personnel, and end-users.
Assign everyone privileges that correspond to their roles and consider it a violation of the security policy if they’re exceeded without verifiable authorization.
3. Encrypt communications
Any internal communication you’re transmitting over a network should be encrypted by default, regardless of its level of sensitivity.
Features like SAP’s ASE encryption provide a good starting point, but they shouldn’t be where you stop. Your SAP systems are likely a core part of your business, making all of their information channels a target for attackers.
4. Maintain backups
Backups are ideal for maintaining business continuity in the event of a catastrophic security incident like a ransomware attack.
By having an uncompromised state that you can revert to as you deal with the incident, you can keep your operations going.
5. Implement patches as soon as possible
Unpatched systems are the second biggest threat to SAP systems. This makes sense when you find out that companies have a patch rate of only 36%. Staying safe requires companies to keep up with all relevant patches for critical security risks.
Patching, however, is only one aspect of vulnerability management, with shortcomings that include long development times and the inability to combat zero-day vulnerabilities. Spinnaker Support third-party support services fill in the security gaps that vendor-issued patches simply can’t.
6. Provide education and training
Your team members should receive ongoing training on identifying and dealing with cybersecurity threats to mitigate the risk of human error.
The initial attack vectors that rely on human error are some of the costliest, with phishing at $4.76 million per breach, social engineering at $4.55 million, and cloud misconfiguration at $4 million.
Depending on what each person’s role in the company is, the education should encompass areas such as security awareness, secure coding practices, access controls, incident response procedures, and relevant regulatory and compliance requirements.
How Spinnaker Support can monitor your SAP systems and much more
SAP’s own security is already costly, but its prices are rising, and it still might not be enough to secure your IT systems.
In contrast, Spinnaker Support provides managed services for SAP systems, which gives you access to:
- Level 2 and 3 engineers, available 24/7/365, with Level 4 on standby for escalation.
- Staff augmentation to fill in any gaps in your security team without going through a lengthy hiring process.
- System health checks to diagnose and address issues as soon as possible.
- Technical managed services and application managed services (TMS and AMS) to cater to your operational and developmental security needs.
- Day-to-day IT management so you can focus on other areas of your company.
- Integration and interoperability to ensure that all interconnected systems are secure.
- Cost-effective services that are over 50% cheaper than first-party offerings.
- Legacy software support so you’re not vulnerable when running software past its end-of-life (EOL) date.
For a more specific offering, look to Spinnaker Shield, a comprehensive approach to vulnerability management that offers:
- Security assessments
- Audit compliance
- Customized security support
- Security tooling
- Security bulletins
- Vulnerability management
Stay ahead of SAP security threats with Spinnaker Support
Relying on first-party security from SAP could mean you’re unknowingly leaving your IT system vulnerable.
By switching to third-party SAP security services from a partner like Spinnaker Support, you get access to timely patches, quick response times, and cost savings. This also gives you the option to continue using legacy software past its EOL, rather than bowing to pressure from the vendor to upgrade.
Contact the team at Spinnaker Support to find out how you can secure your SAP systems comprehensively and on your own terms.


