Though attack surfaces and attack vectors are often confused with each other, there’s a lot of difference between the two terms. If you want to assess and prioritize security measures more effectively, it’s crucial to understand how they differ.
By understanding the attack surface, you can identify and mitigate security vulnerabilities in a system. Understanding the attack vector allows for targeted security measures to prevent unauthorized access.
Differentiating between the two enables a comprehensive approach to cybersecurity, reducing the risk of successful attacks.
This article will help you understand an attack surface and an attack vector, with examples. We’ll also share how Spinnaker Support, our third-party support service, can help you strengthen your security posture.
Attack surface vs. attack vector: What are the differences?
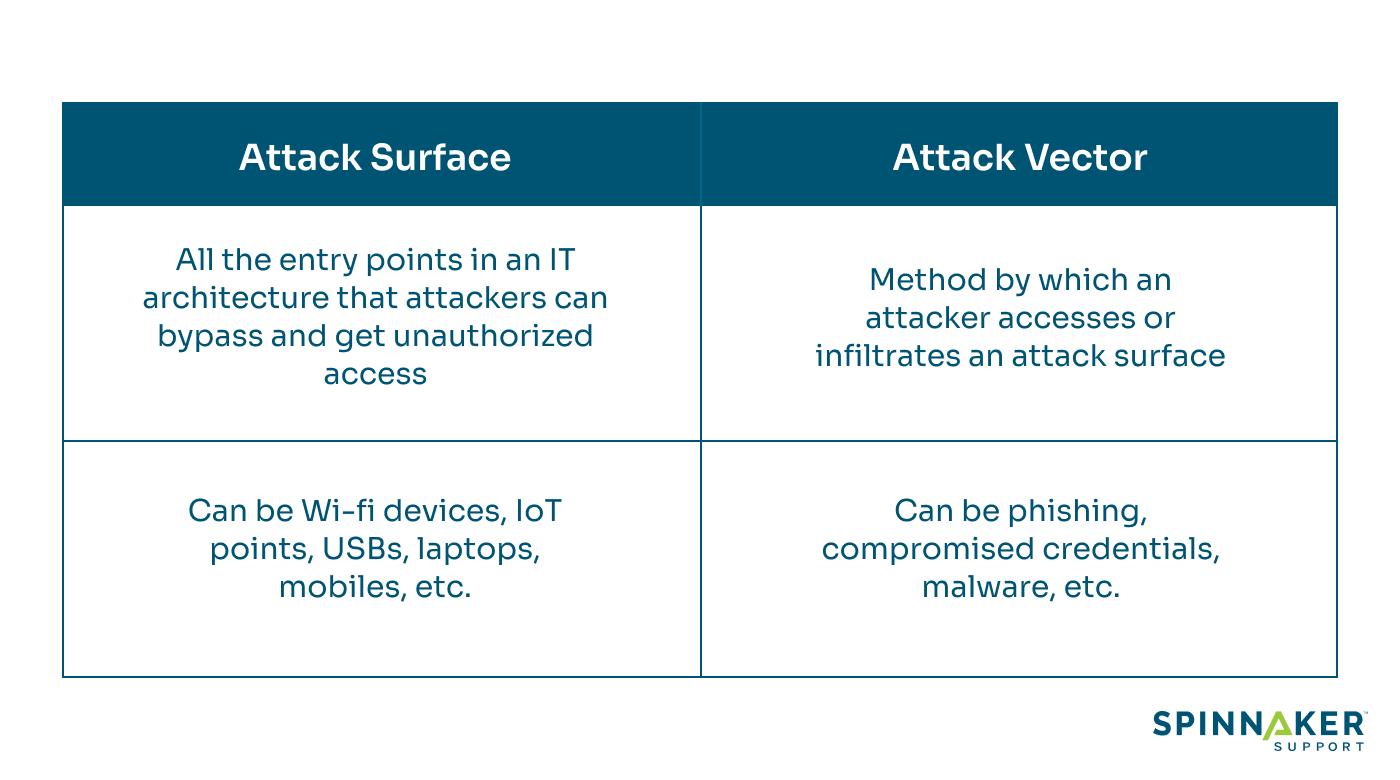
An attack surface is the sum of all of the points on your enterprise network where an attacker can attempt to gain unauthorized access to your information systems. At the same time, an attack vector is the specific attack route, whether through the network or OS.
What is an attack surface?
Attack surface refers to the exposed vulnerabilities in a system. It’s the sum of all the possible entry points or weak spots in an application, network, or infrastructure that potential attackers can target and exploit.
Here are a few examples:
- Network interfaces: Ports, firewalls, and routers.
- User interfaces: Web applications or APIs.
- Third-party integrations: Any external system connected to the main application.
What is an attack vector?
An attack vector refers to an attacker’s specific method to infiltrate through an opening in security defenses in an attack surface.
An attacker gains unauthorized access or compromises a system — the path can depend on the target and the techniques employed by the attacker.
Here are a few examples of different types of attack vectors:
- Phishing: Trick users into revealing sensitive information through deceptive emails or websites.
- Malware: Infected files or malicious websites can deliver viruses, worms, or trojans.
- Social engineering: Attackers manipulate individuals to disclose confidential information or perform certain actions.
You can strengthen attack vectors by adopting hardening control measures like installing patches, upgrading operating systems, and running vulnerability scans.
Working with a third-party support provider like Spinnaker Support can be beneficial here.
We use a Defense-in-Depth approach that goes beyond just replacing patches and updates. We proactively spot weaknesses and suggest attack surface reduction measures. We also help mitigate risks with enhanced processes and best practices.
Attack surface vs. attack vector: Real-world examples
Let’s understand more about an attack surface and an attack vector with case studies.
Here are two real-world examples of attack surfaces and attack vectors.
Attack surface real-world example: Milesight (Ursalink)
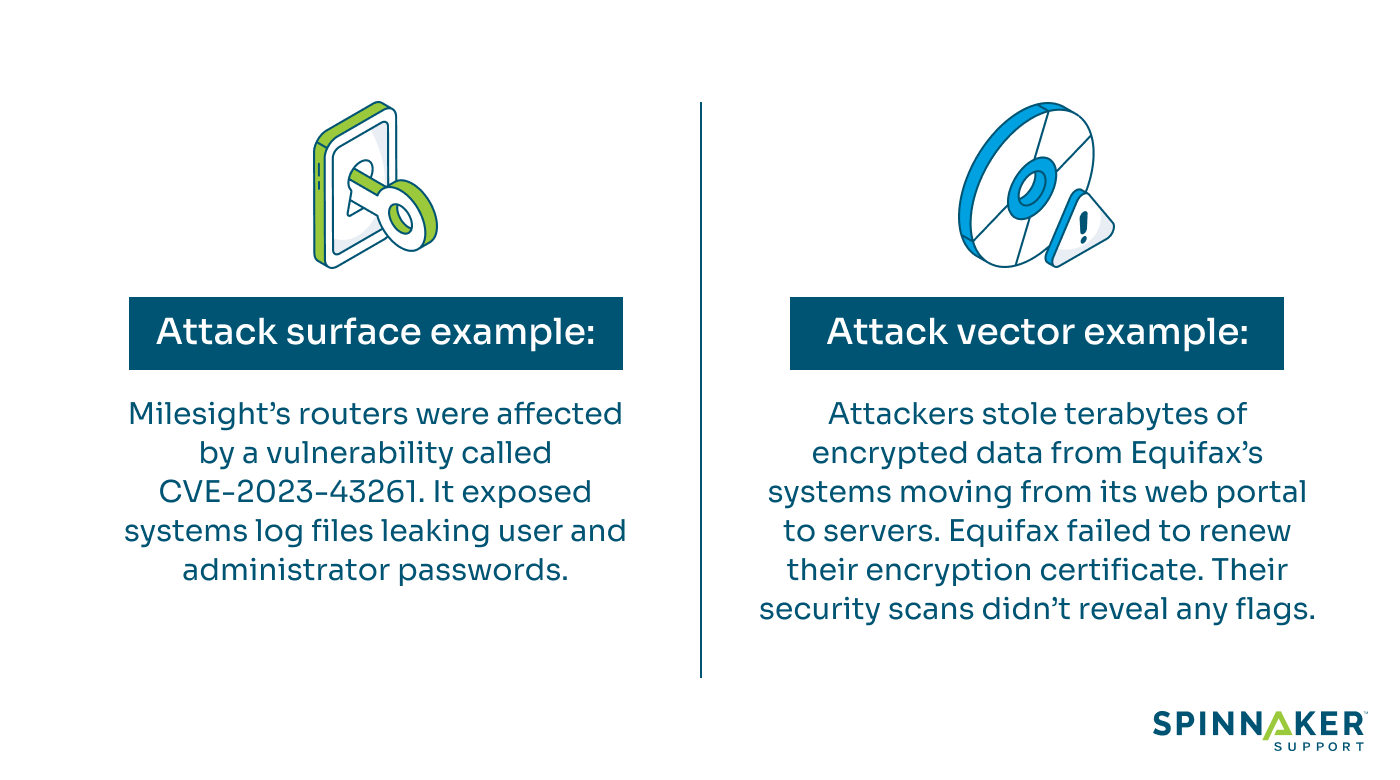
Milesight’s industrial routers were hit by vulnerabilities that exposed system log files. Attackers captured the passwords of administrators and users via unauthorized access.
This meant the routers had a vulnerable web server component that allowed unauthenticated remote code execution. In this case, the attack surface was Milesight’s industrial routers.
Attack vector real-world example: Equifax
In 2017, Equifax, one of the largest credit reporting agencies in the US, experienced a significant data breach that exposed the personal information of about 143 million individuals. This case study serves as an example of an attack vector that attackers exploited.
The attack vector used in the Equifax breach was a vulnerability in the Apache Struts web application framework. The attackers discovered a flaw in Apache Struts software and exploited it to gain unauthorized access to Equifax’s systems. They were able to infiltrate the company’s networks and extract sensitive data like names, social security numbers, birth dates, and credit card information.
What are the different attack surface types?
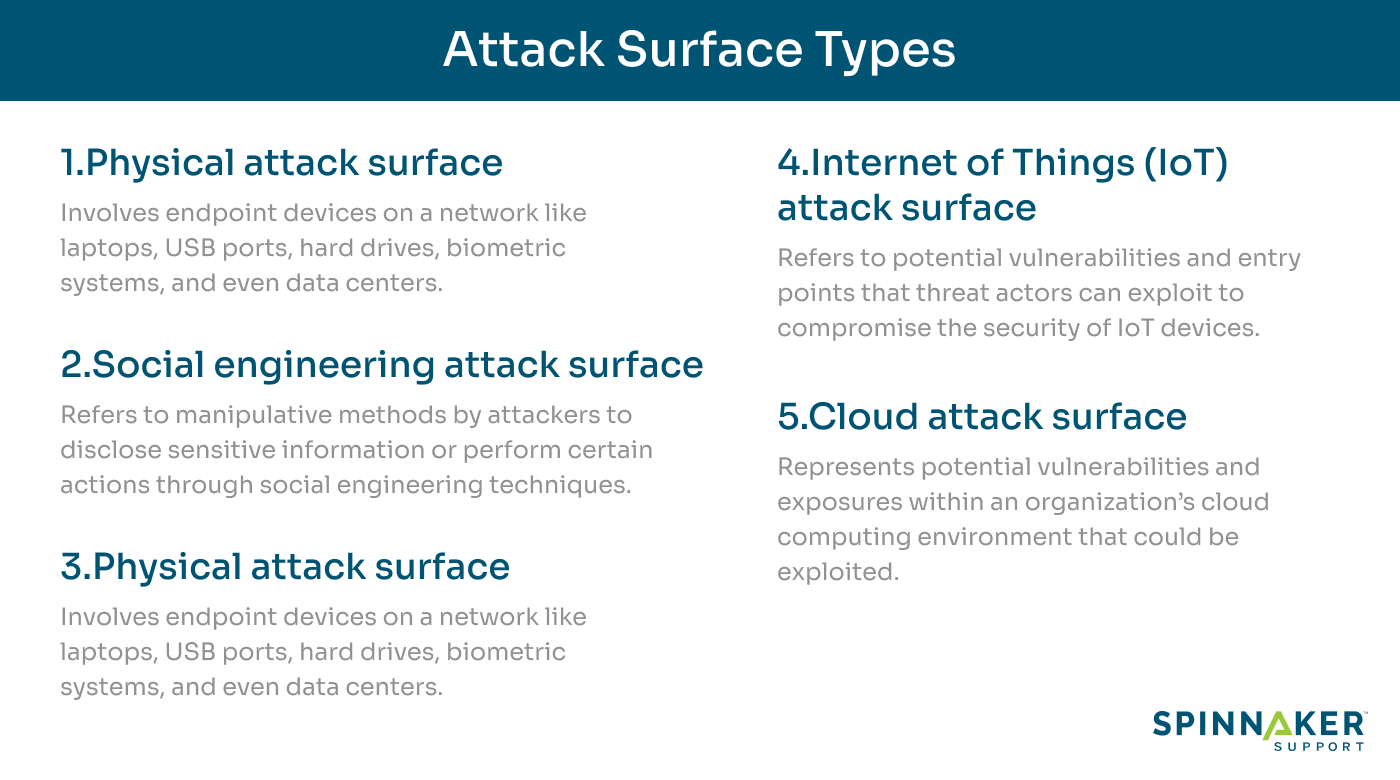
Organizations face security threats across five key attack surfaces — physical, social, digital, Internet of Things (IoT), and the cloud.
Here’s a look at each attack surface type.
Physical attack surface
The physical attack surface refers to tangible, real-world access points and aspects like:
- Office security
- Improperly disposed documents
- Unsecured computers and devices, and
- Vulnerable entry points to facilities
For example, an attacker could physically breach a building or room to steal data or tap into the network.
Social engineering attack surface
The social engineering surface covers the ways attackers trick or fool employees.
Typical attacks include phishing emails, fraudulent phone calls, and impersonators. Employees often give away passwords or grant access due to deception.
Digital attack surface
The digital attack surface involves virtual entry points in software, applications, and online accounts.
Vulnerabilities like unpatched bugs, misconfigurations, and unprotected APIs can allow remote exploitation. Attackers scan for and penetrate exposed digital surfaces.
Internet of Things (IoT) attack surface
The IoT surface constitutes the growing number of smart, internet-connected devices like thermostats, automated checkouts, and assembly lines open to threats. IoT devices often lack proper security controls. Attackers can exploit them as backdoors into corporate systems.
Cloud attack surface
The cloud attack surface consists of improperly configured cloud resources and permissions errors. As organizations adopt cloud services, they increase exposure if not properly secured.
How to assess your attack surface
Now that we know the different types of attack surfaces, how can we assess them?
Follow these steps.
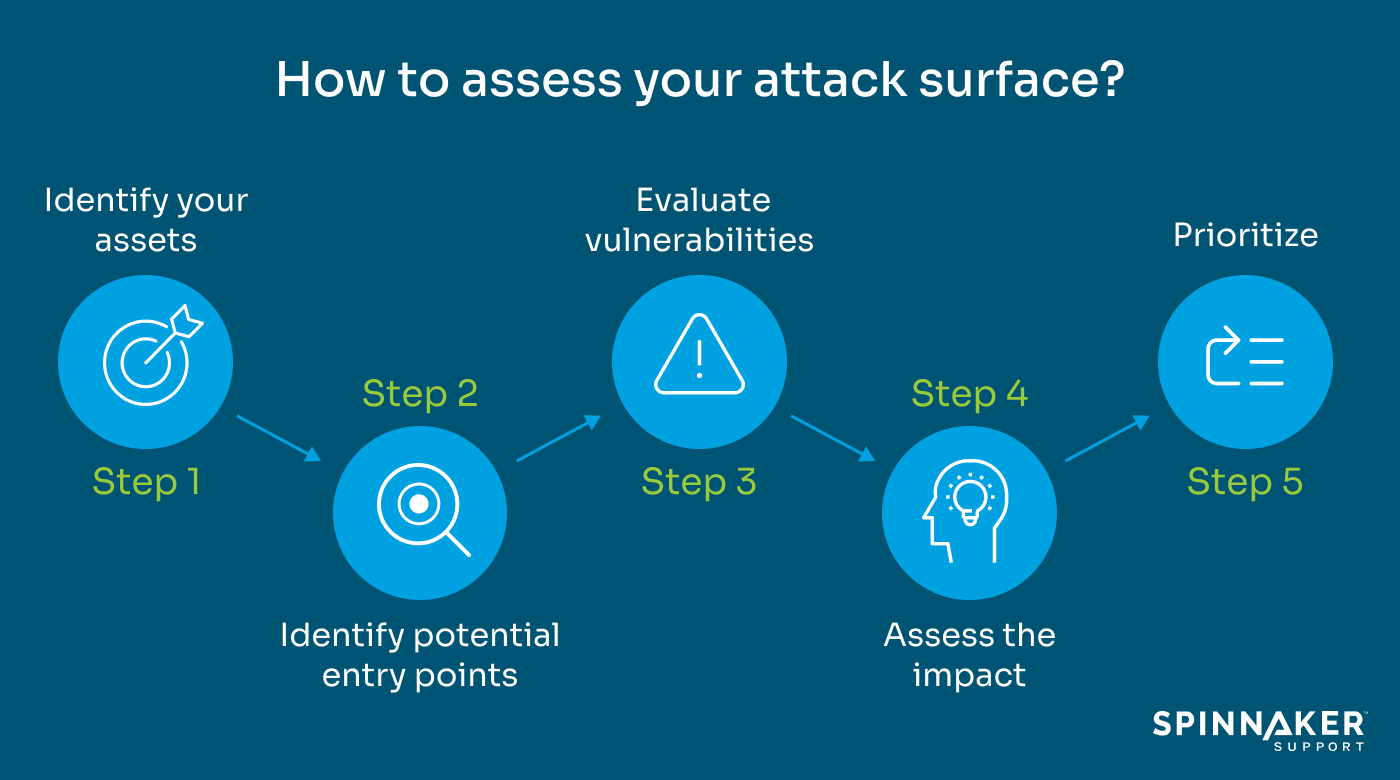
Step 1: Identify your assets
Make a list of all the assets in your system that are valuable or vulnerable to attack. This includes hardware devices, software applications, databases, networks, and any other components that you feel attackers can target.
Step 2: Identify potential entry points
Determine all the possible ways an attacker could gain unauthorized access to your system. This includes analyzing network interfaces, user interfaces, third-party integrations, and any other points of interaction or connection.
Step 3: Evaluate vulnerabilities
Conduct a thorough analysis of each identified entry point to determine potential vulnerabilities.
Here are some examples that you may encounter during the evaluation process:
- Outdated and unpatched software or firmware
- Easily guessable weak passwords
- Faulty security settings
- Inadequate encryption protocols
- Unpatched security vulnerabilities
- Inadequate access controls and permission systems
- Poorly implemented authentication mechanisms
- Lack of monitoring or logging capabilities
Due to cloud adoption and interoperability, organizations can find it difficult to manage security. In such cases, you can take the help of Spinnaker Support’s holistic security offerings.
Our security experts understand the threat of common vulnerabilities and exposures (CVE). We investigate issues and protect your environment while delivering timely remediation. We also advise you on how to comply with regulations like SOC 2 and GDPR.
Step 4: Assess the impact
Determine the potential impact of a successful attack on each vulnerability. Consider factors such as data loss, unauthorized access, financial loss, reputation damage, and regulatory compliance.
Step 5: Prioritize
Assign a risk level to each vulnerability based on its likelihood of being exploited. Prioritize vulnerabilities based on their potential impact and the resources available for mitigation. Focus on addressing high-impact vulnerabilities first to minimize the risk to your system.
10 ways to reduce your attack surface area
Minimizing attack surfaces is key to strengthening an enterprise security posture. By shrinking the opportunities attackers have to gain access, organizations can better defend their critical assets and data.
Here are some ways to do that.
Minimize unnecessary services
Only run the essential services for the system’s functioning and disable or remove unused or unnecessary services (like closing unused TCP ports). Also, reduce the number of codes running.
Adhering to the principle of least functionality by minimizing services to block openings and limit lateral movement. This forces them to take a more obvious path, allowing defenses to concentrate.
Keep software up to date
Organizations address known potential vulnerabilities by promptly installing patches, upgrades, and new versions when vendors release them.
Use strong authentication
Implement strong authentication mechanisms, such as multi-factor authentication and biometrics, to prevent unauthorized access.
Implement strong password policies
Enforce a strong password policy that includes complexity requirements and regular forced password changes.

Requirements like minimum length, use of special characters, and banning common or reused passwords raise the bar for attackers attempting to brute-force into accounts.
Restrict user privileges
Follow the principle of least privilege, granting users and systems only the necessary permissions and access rights required to perform their tasks. You can also implement role-based access controls (RBACs).
Implement network segmentation
Divide the network into smaller segments with separate access controls to contain potential attacks and limit their spread.
Use firewalls and intrusion detection systems
Set up firewalls to filter incoming and outgoing network traffic and use intrusion detection systems to track suspicious activities.
Use third-party support
With Spinnaker Shield’s services, you can work with professionals who can advise on strengthening controls to defeat potential attack vectors. We do this with an in-depth approach, as shown in the image below.
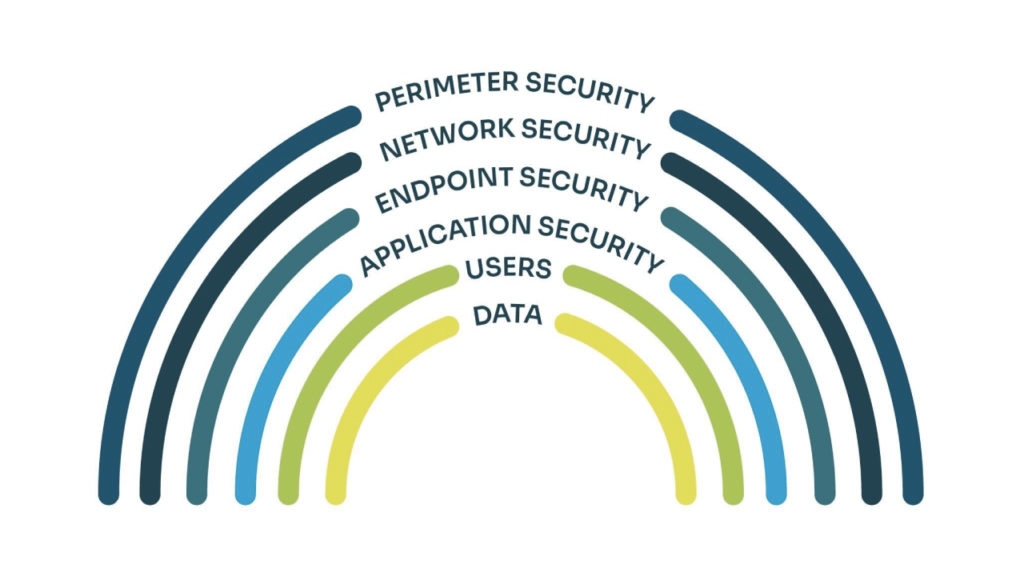
For example, we performed a vulnerability scan for a large civic body. In the reports, we highlighted several security issues, like improper use of firewalls, and advised them to correct them. However, they didn’t implement the recommended actions, and their systems were subsequently attacked within a week. Our team instantly analyzed the attack vector and applied specific recommendations from the report.
Follow best practices
Encrypt sensitive data in transit using secure protocols such as HTTPS or VPNs to protect it from interception.
Perform regular backups of critical data to ensure that it can be restored in the event of a compromise or data loss.
Provide regular training to employees on cybersecurity best practices, such as recognizing phishing emails and maintaining strong passwords.
Conduct regular security assessments
Regularly assess the system’s security through vulnerability scans, penetration testing, and security audits to identify and address weaknesses. Create incident response plans to get to action quickly once an attack happens.
Common FAQs for attack surface vs attack vector
Have more questions about attack surfaces and attack vectors? Here are answers to frequently asked questions.
What is the difference between an attack tree and an attack surface?
An attack tree is a visual model that outlines the various ways an attacker could take to achieve their goal of compromising a system or network step-by-step. It represents different attack paths as branches, with the root node being the objective.
On the other hand, the attack surface consists of existing flaws, gaps, and weaknesses across an environment that real-world attackers could leverage to gain access right now.
An attack tree does risk analysis, but minimizing the attack surface directly strengthens real-world defenses.
What is the difference between an exploit and an attack vector?
An exploit is a piece of code or a specific action that exploits security flaws in systems and configurations. An attack vector is a general path and an entry point an attacker takes to gain access to the target system.
Exploits are tactical, but attack vectors are strategic. Multiple exploits can be a part of implementing a single attack vector.
What is the most common attack vector?
Phishing is the most common attack vector.
In a phishing attack, bad actors pretend to be a trusted source and trick people into giving away sensitive information or downloading malware. They do this by sending fake emails, websites, calls, or messages that look real. Other two common attack vectors are credential abuse and exploitable software vulnerabilities.
Reducing attack surfaces requires an ongoing, layered approach
Minimizing attack surfaces requires comprehensive diligence, given constantly evolving cyber threats.
While organizations can implement least-privilege access and prompt patching, protecting the entire attack surface benefits from partnering with managed service providers like Spinnaker Support.
Our Spinnaker Shield security offers ongoing vulnerability, surface area management, and penetration testing. Organizations can best reduce attack surfaces by having internal staff and external partners work together. This helps find risks and makes defenses stronger against different hacking methods.
If you would like any information on Spinnaker Support or our support and services, please reach out to us today!


