The Health Insurance Portability and Accountability Act (HIPAA) defines standards that healthcare organizations must follow to protect sensitive patient information. Healthcare providers can mitigate risks, prevent costly data breaches, and maintain patient trust by adhering to HIPAA regulatory requirements.
This article will illustrate the common pain points associated with HIPAA compliance and offer you a comprehensive checklist to help address them. Implementing a practical HIPAA compliance checklist makes life easier as you work to ensure that protected health information (PHI) remains secure and confidential.
We’ll also share top strategies for how healthcare organizations can navigate the complex landscape of HIPAA regulations, including the benefits of enlisting third-party support (3PS).
What is HIPAA compliance?
HIPAA compliance is achieved when your digital systems adhere to the security and privacy standards set forth in the Health Insurance Portability and Accountability Act.
The purpose of HIPAA compliance is to ensure the privacy and security of the sensitive PHI in patients’ digital healthcare records. Compliance typically entails ongoing efforts by cybersecurity and IT teams to maintain a hardened state of network security,
Several types of US healthcare organizations are required by law to obey HIPAA regulations, including:
- Covered entities are any healthcare provider conducting certain electronic transactions, health plans, and healthcare clearinghouses. This includes hospitals, clinics, pharmacies, and health insurance companies.
- Business associates are individuals or organizations that work with covered entities and can access PHI. This can include IT vendors, billing companies, transcription services, and more.
- HIPAA regulations also apply to subcontractors of business associates who handle PHI. Covered entities and business associates must take special care to ensure that all PHI parties comply with HIPAA regulations.
Note: Find in-depth information on the purview of HIPAA here.
PHI contains sensitive information about an individual’s health, which could have disastrous consequences if exposed, such as fraud, privacy breaches, and identity theft. Safeguarding PHI is therefore crucial to protect patients’ rights and maintain trust in the healthcare system.
It’s also in your company’s best interest to maintain compliance. As of 2023, the penalties for HIPAA violations could be as much as $68,928 for a single violation – or up to $2,000,000 for a violation that goes unaddressed.
Sadly, we’ve seen a recent increase in PHI breaches.
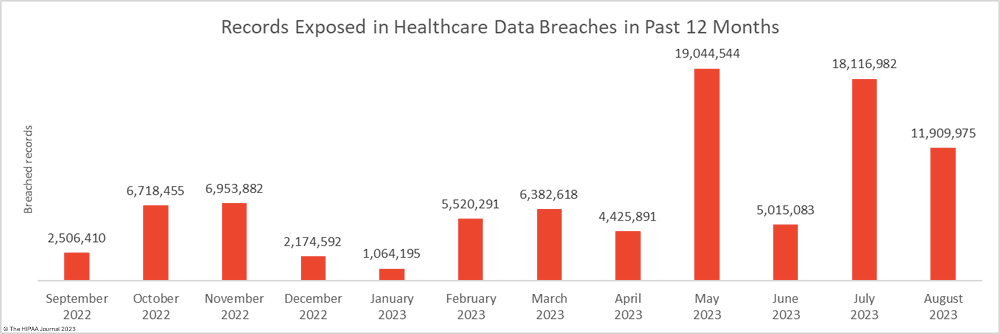
In the face of escalating risk, it’s more important than ever that healthcare organizations implement robust practices to safeguard PHI.
HIPAA compliance checklist
A HIPAA compliance checklist is essential because it provides healthcare organizations with a systematic approach to identifying potential vulnerabilities, implementing necessary safeguards, and monitoring ongoing compliance efforts.
We’ll cover each step in detail, below.
Analyze risk
Perform a risk analysis to identify potential vulnerabilities in your system. This lets you know where you can take action to effectively shore up your security and handling of sensitive health information.
Analyzing risk is also essential to prevent expensive data breaches.

Some key activities that you can do at this step are:
- Test the efficiency of current security controls and safeguards
- Identify vulnerabilities in the system, such as outdated software or weak passwords
- Assess the impact and risk of data breaches or unauthorized access
- Create a risk management plan that defines solutions for mitigating the identified risks
Establish security policies
Security policies are documents that explicitly spell out a company’s plans for protecting its IT assets. In the healthcare sector, your policies should define steps to ensure HIPAA compliance.
Some potential action items to consider include:
- Develop a comprehensive set of security procedures for handling and protecting PHI
- Define roles and responsibilities for staff members involved in handling PHI
- Train employees on how to manage and dispose of PHI and how to adhere to other privacy and security best practices
- Implement procedures for securely transmitting and storing PHI, including encryption and secure data storage
- Review and update policies regularly so that they are up to speed with current regulations
- Audit security policies periodically to ensure they are effective
Implement safety practices
Implement strong safety practices that will limit access to PHI only to authorized individuals who have a legitimate need to know.

Some facets of safety to consider include:
- Access controls: implement controls that ensure only authorized users can access PHI. Consider requiring unique usernames, complex passwords, and two-factor authentication.
- Audit controls: monitor access to PHI by logging user activity and regularly reviewing activity logs
- Encryption: use data encryption to protect PHI both in transit and in storage.
- Physical safeguards: Implement measures to secure datacenters and other physical locations where PHI is stored, including surveillance systems and secure storage containers.
- Incident response: Maintain readiness for IT teams to quickly respond to and mitigate any security incidents that occur. To strengthen your team, consider engaging proactive third-party security support.
Train employees on regulations
Regular training helps employees stay up-to-date with evolving HIPAA regulations, ensuring ongoing compliance.
- Develop training materials that help employees understand HIPAA regulations and their personal responsibilities.
- Conduct workshops to educate employees about HIPAA regulations, privacy requirements, and best practices for handling PHI.
- Provide practical, hands-on training for the daily procedures employees will use for securely accessing, storing, and transmitting PHI.
- Track and monitor employees’ training completion to ensure all staff members receive the necessary education on HIPAA regulations.
- Offer refresher training sessions to ensure employees stay updated with HIPAA regulation changes.
Create documentation
Documenting everything is crucial for HIPAA compliance because:
- It provides evidence of compliance. Documentation serves as proof that you are following HIPAA regulations and helps demonstrate your efforts to maintain the security and privacy of PHI.
- It ensures consistency. Clear and comprehensive documentation ensures that your organization follows the same protocols and procedures for handling PHI.
- It aids in audits and investigations. In the event of an audit or investigation, documentation can help streamline the process and demonstrate your commitment to compliance.
- It facilitates training and awareness. Documentation can be used as training material to educate employees on HIPAA requirements.
Monitor and audit compliance efforts
To ensure you remain in ongoing compliance with HIPAA regulations, you must conduct frequent internal audits.
- Review policies and procedures to ensure they align with current regulations.
- Scan network systems for “compliance drift,” or unintentional changes in configuration that can result in noncompliance. This is important because these vulnerabilities may otherwise go unnoticed and network attacks are the most common form of HIPAA breaches.
- Mitigate any identified compliance gaps or issues through corrective actions.
A qualified third-party support provider like Spinnaker Support can help you with everything you need to maintain good security and compliance posture.
Our offering, Spinnaker Shield, helps you with risk mitigation and vulnerability management. Our experts investigate and harden your security systems with a “Defense in depth” approach. We provide consultation on properly addressing IT risks and share industry best practices. Then, we also adjust your controls so that you stay compliant.
Understand rules
As you navigate HIPAA compliance, you’ll need to understand these three central rules.
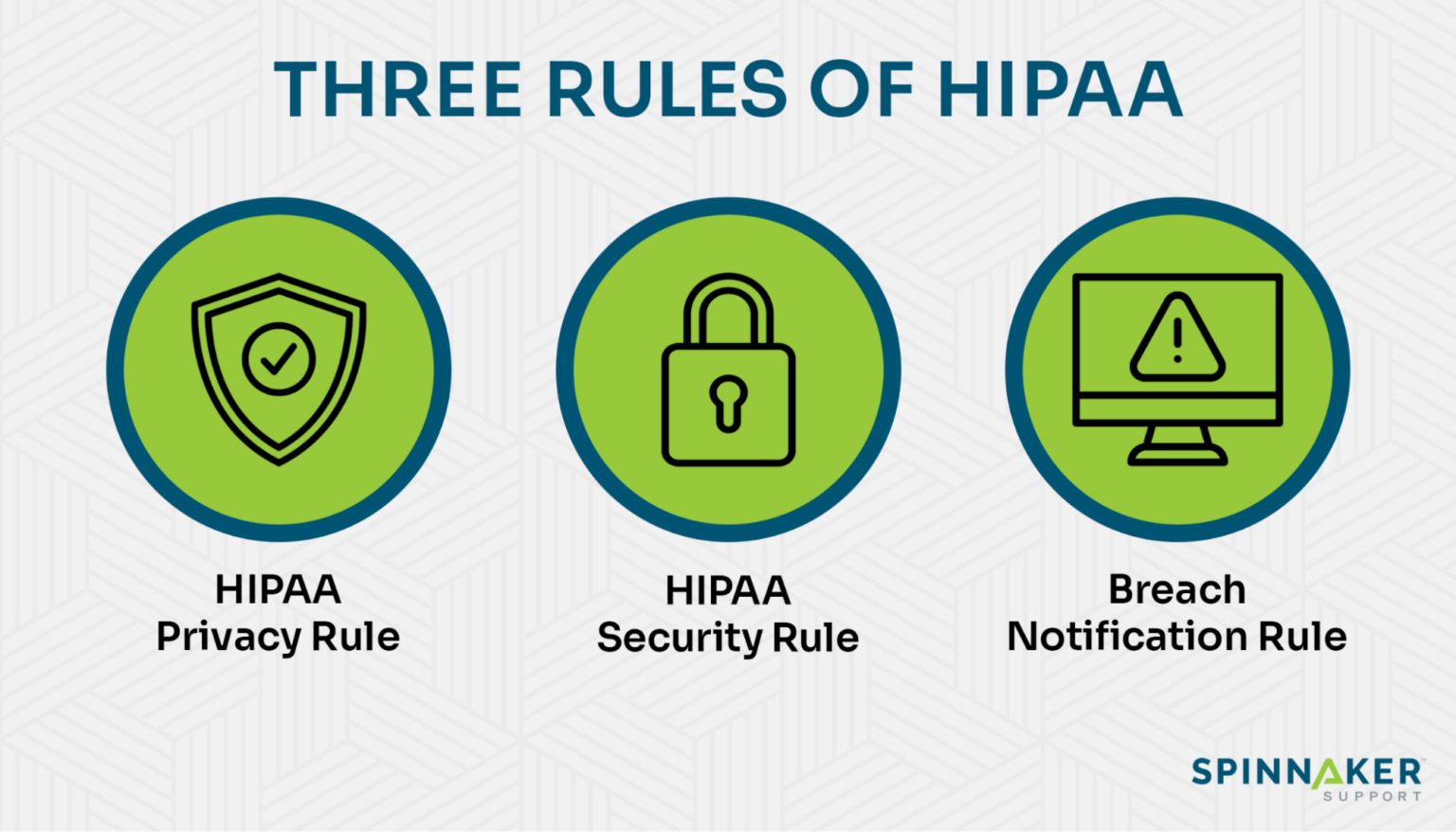
- Privacy Rule establishes standards for protecting individuals’ medical records and other personal health information. It also gives patients the right to validate their records and request corrections.
- Breach Notification Rule requires covered entities to notify affected individuals in the case of a breach. You may also be required to notify the Secretary of Health and Human Services, and, in some instances, the media.
- Enforcement Rule requires covered entities to implement safeguards to protect electronic health information. It also outlines the procedures for investigating and enforcing HIPAA compliance.
Note: You can learn more about the intricacies of these rules here.
Know about safeguards
Learn about the safeguards that ensure compliance and maintain data confidentiality. Some of these include:
Administrative safeguards: These involve the development of policies and procedures for handling protected health information (PHI), conducting risk assessments, and training employees on HIPAA regulations.
Physical safeguards: These focus on securing the physical environment where PHI is stored or accessed.
Technical safeguards: These involve implementing technology solutions to protect PHI, such as encryption, firewalls, and access controls.
Organizational safeguards: These address the policies and procedures for managing business associates, establishing contracts, and conducting audits.
HIPAA compliance challenges
Achieving HIPAA compliance has its challenges. We will explore some common hurdles that organizations face in maintaining HIPAA compliance.
Lack of awareness
Many healthcare organizations and individuals may not understand the requirements and regulations outlined by HIPAA, leading to non-compliance.
You can foster awareness with training and leadership initiatives. You can also enlist the help of teams who already have expert knowledge of HIPAA compliance practices, such as the support specialists at Spinnaker Support.

Complexity of regulations
HIPAA regulations can be hard to interpret, especially for smaller healthcare providers without dedicated compliance officers.
Data security
Safeguarding patient data and ensuring its privacy is a constant challenge, as healthcare providers must strengthen their security measures to prevent breaches or other cybersecurity frauds.
Technology implementation
Adopting and implementing the necessary technology systems and tools to ensure HIPAA compliance can be expensive and time-consuming for healthcare organizations.
It requires integrating secure data storage, encryption, and other security measures. Legacy systems and outdated technology can challenge electronic protected health information (ePHI) security.
If you’d like to update your legacy systems but don’t know where to begin, you can avail Spinnaker Support’s advisory services. Our experts have 20+ years of experience and will guide you on what roadmap to take.
In addition, if you’re already using a CRM or ERP system and want to achieve massive cost savings, our 3PS can help you reduce your support costs by 60%. OEM support is expensive and may not be comprehensive. In contrast, with Spinnaker Support, you can get holistic support at a reduced cost and troubleshooting help via Level 3 and Level 4 engineers.
Vendor management
Healthcare organizations often rely on third-party vendors for electronic health record systems, cloud storage, SaaS delivery, and other features. However, managing these vendors and ensuring their compliance with HIPAA regulations can be challenging.
Changing landscape
The healthcare industry is dynamic, with new technologies and regulations constantly emerging. Adapting to these changes and staying in the know can be challenging for organizations to maintain HIPAA compliance.
You might want to enlist professional help to keep up with regulatory updates.
For example, consider this success story from Spinnaker Support. Our client created a breakthrough technology that allowed in-home patient care — anywhere, anytime. However, the company couldn’t comply with HIPAA and PHI requirements and had to pause all work for three months.
Spinnaker helped this client satisfy all their HIPAA requirements and get back to work. First, we implemented encrypted data in transit. Then, we strengthened their security controls and enhanced their security layers. We helped them execute a roadmap to satisfy all other HIPAA compliance requirements and set them up to stay on track moving forward.
Simplify your HIPAA compliance efforts
A comprehensive HIPAA compliance checklist is essential for healthcare organizations to protect sensitive patient information.
Consider working with third-party support like Spinnaker Support to ensure all necessary measures are in place and the organization remains up to date with any changes in regulations.
3PS can help healthcare organizations stay on top of potential cybersecurity threats and implement the latest technologies and strategies for better security.
Contact us to learn more about how Spinnaker Support can help your healthcare organization with compliance, security, and more.


