
Poor security posture can make your IT infrastructure vulnerable to cyber threats and data breaches, which can result in lost revenue and damage your brand reputation.
Understanding how Common Vulnerabilities and Exposures (CVE) and Common Weakness Enumeration (CWE) work can help companies address vulnerabilities and harden their IT infrastructure.
In this article, we’ll explain what CVE and CWE are and explain the differences between the two. We’ll also look at how you can shore up your security with Spinnaker Shield.
What is CVE?
CVE stands for Common Vulnerabilities and Exposures. It’s a directory containing a list of known security vulnerabilities and common software weaknesses that attackers can exploit for personal gain.
The CWE database is maintained by the MITRE Corporation, an American non-profit that works with federal agencies. It contains over 200,000 records and is freely available to the public.
Searching for a keyword like “Apache” in the CWE database allows you to view relevant results:
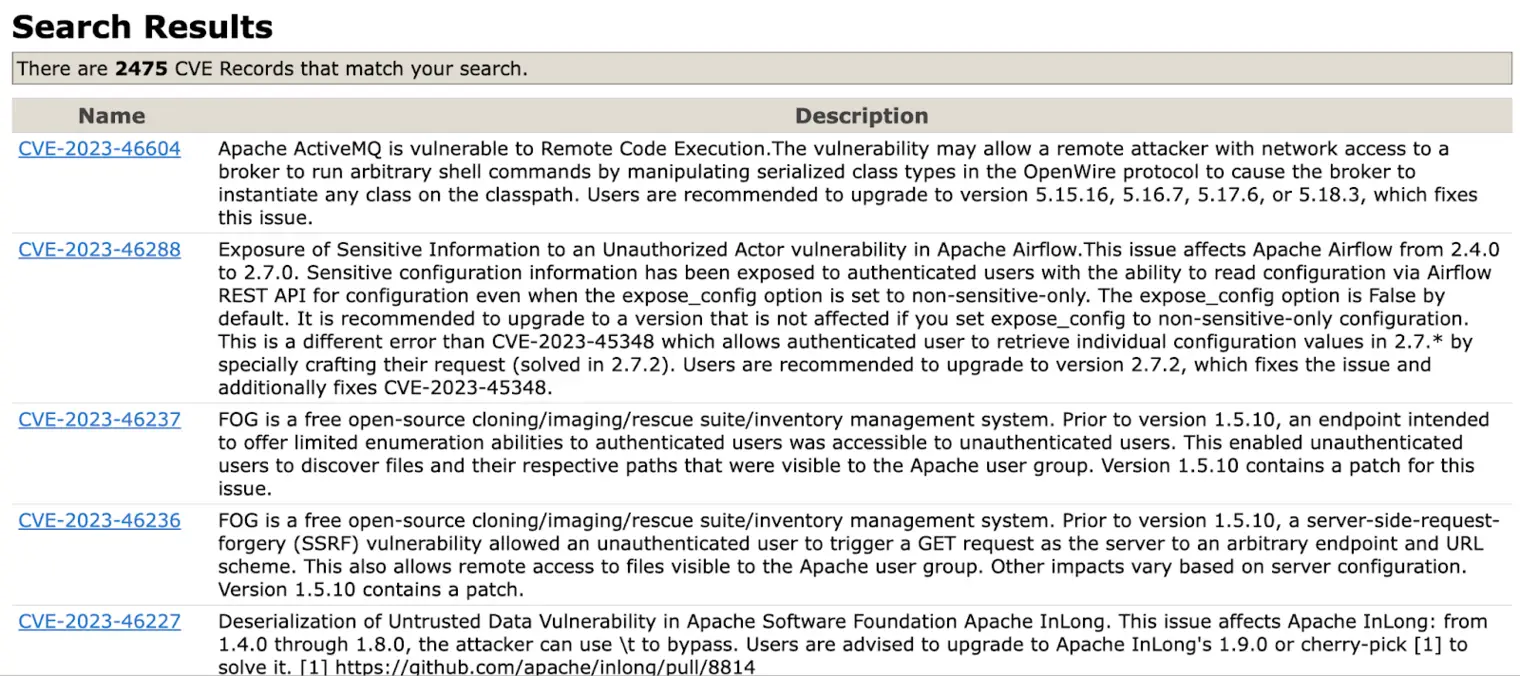
While the MITRE Corporation maintains the CVE list, the organization doesn’t actively search for new vulnerabilities. Reports come from researchers, vendors, and even users who may discover a critical exploit while using a software product. The CVE Numbering Authority (CNA) assigns CVEs to newly discovered vulnerabilities and posts them to the CVE list.
Software developers can use the CVE database to identify known vulnerabilities in the software they’re working with. They can address these by installing patches or changing configurations before they manifest as issues.
What qualifies as a CVE?
A software vulnerability must meet certain criteria before qualifying as a CVE. This helps distinguish between bugs and vulnerabilities.
A vulnerability may qualify as a CVE if:
- It exists in a commercial or open-source product: CVEs are only assigned to publicly available products. This includes software, firmware, and hardware.
- It’s publicly disclosed: A vendor has acknowledged the vulnerability, or a reporter has shared a report that discloses how it violates a vendor’s security policy.
- It has a potential security impact: An attacker can exploit the vulnerability and perform unauthorized actions.
- It’s independently fixable: It must be possible to fix or remediate a vulnerability independently from other issues.
- It affects one piece of software: A vulnerability that affects more than one product or codebase receives multiple CVEs.
The following graphic shows how vulnerabilities are published as CVEs:
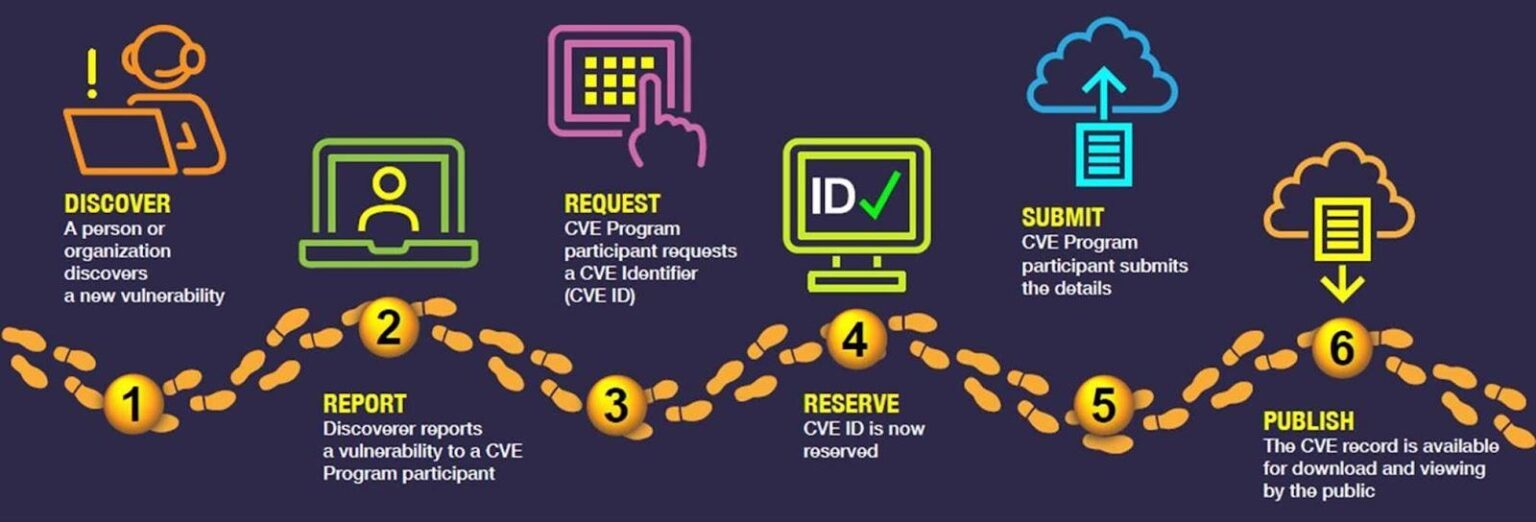
CVEs aren’t always published immediately, even if a vulnerability qualifies as one. This gives software vendors time to publish updates before making a CVE public.
What is the Common Vulnerability Scoring System (CVSS)?
The Common Vulnerability Scoring System (CVSS) is an open industry standard that rates CVEs from low to critical based on severity. It helps companies assess and prioritize their vulnerability management processes.
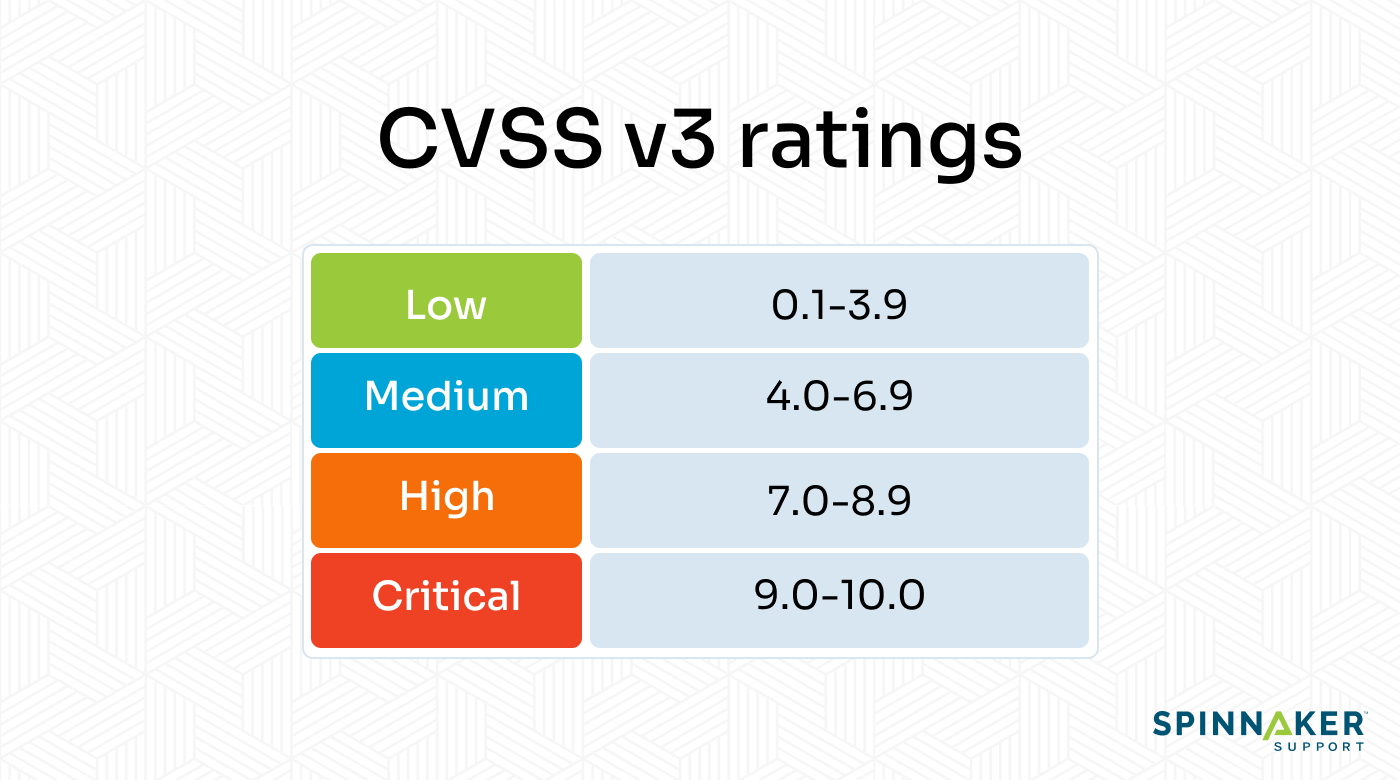
It’s important to address and prioritize critical CVEs before attackers can exploit them. This typically involves installing the latest security patches for the affected software.
At Spinnaker Support, we offer robust security solutions that help harden and protect your IT infrastructure from cyber threats. We adhere to a proven framework that helps proactively maintain a more secure environment.
What is CWE?
CWE stands for Common Weakness Enumeration. It’s a community-developed list of names and descriptions of specific software weakness types. It is a common language that helps facilitate communication between developers and security experts.
The CWE list is also operated and maintained by the MITRE Corporation. Anyone can freely view and download CWE-related data for weaknesses like affected platforms, common consequences, observed examples, etc.
Below, we have CWE-287, classified as an improper authentication — a weakness when a system doesn’t properly authenticate a user.
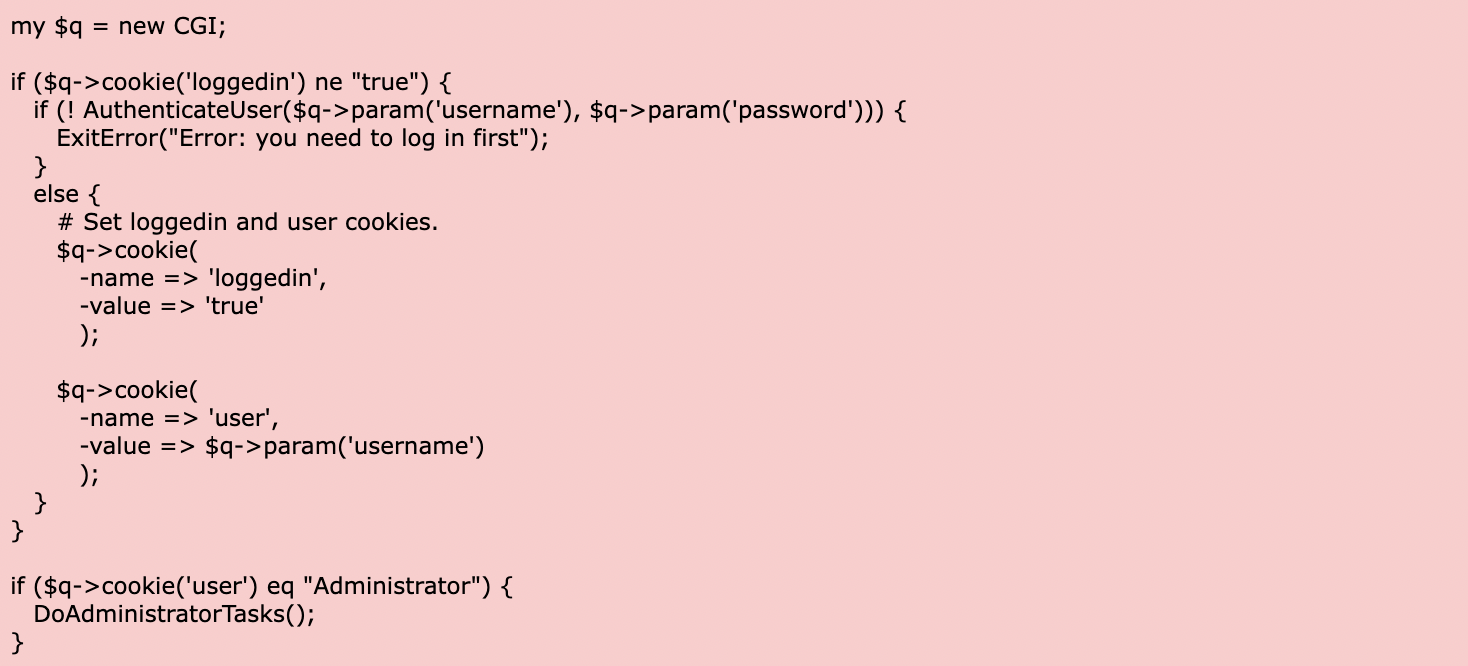
A hacker must place an HTTP request and set the logged-in cookie to “true” to bypass the authentication mechanism. Another example of an improper authentication would be allowing unlimited login attempts, a weakness that hackers can exploit to “brute force” their way into an account by trying new passwords until they’re successful.
Using CWE, developers can proactively identify and address known weaknesses to create more secure software products.
What is the Common Weakness Scoring System (CWSS)?
Not all weaknesses carry the same degree of risk.
The Common Weakness Scoring System (CWSS) is a system that scores the severity of software weaknesses. Like CVSS ratings, organizations can use the CWSS to prioritize threats that pose greater risks to their systems.
The CWSS comprises three metric groups — each containing multiple factors that are used to calculate a CWSS score.
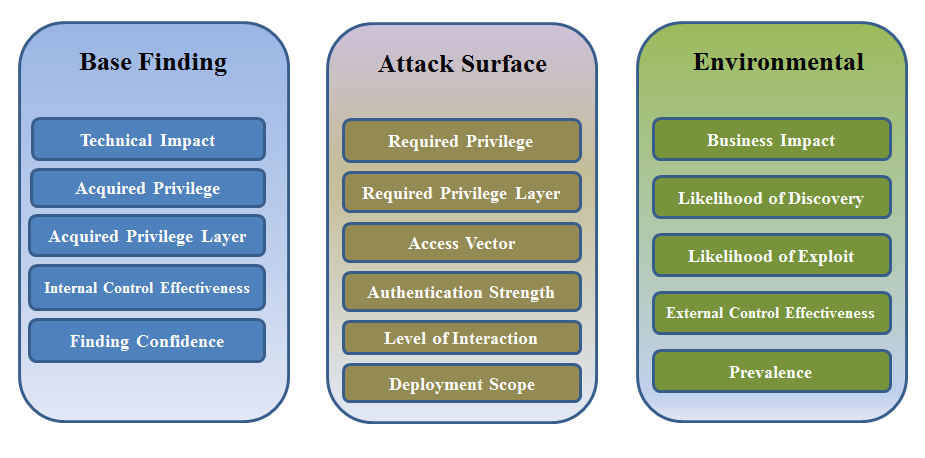
These metric groups are:
- Base Finding: This group focuses on the inherent characteristics of a weakness. It includes factors like technical impact and ease of discovery.
- Attack Surface: This group includes factors that characterize how an attacker can exploit a weakness, such as the privileges needed to execute an attack and the required level of effort or expertise.
- Environmental: This group focuses on the impact on an “environment or operational context.” For example, one factor considers the impact of the confidentiality of data if the weakness is exploited.
Subscores for the Base Finding range from 0 to 100, while Attack Surface and Environmental subscores range from 0 to 1. The subscores are then multiplied, giving a CWSS score from 0 to 100.
You can use a code analysis tool to calculate these scores. Alternatively, you can manually calculate them with a software security consultant.
What’s the difference between CVE and CWE?
CVE refers to a specific software vulnerability.
For example, CVE-2021-34473 is a remote code execution vulnerability that allows attackers to bypass authentication for Microsoft Exchange Server.
The CVE list contains information about this vulnerability, including its CVSS base score, known affected software configurations, and possible fixes.
CWE refers to a software weakness that could lead to a vulnerability.
For example, CWE-787 is an out-of-bounds write weakness that can cause a program to write data to memory outside a buffer boundary. In other words, the program is trying to store data in a place where it shouldn’t.
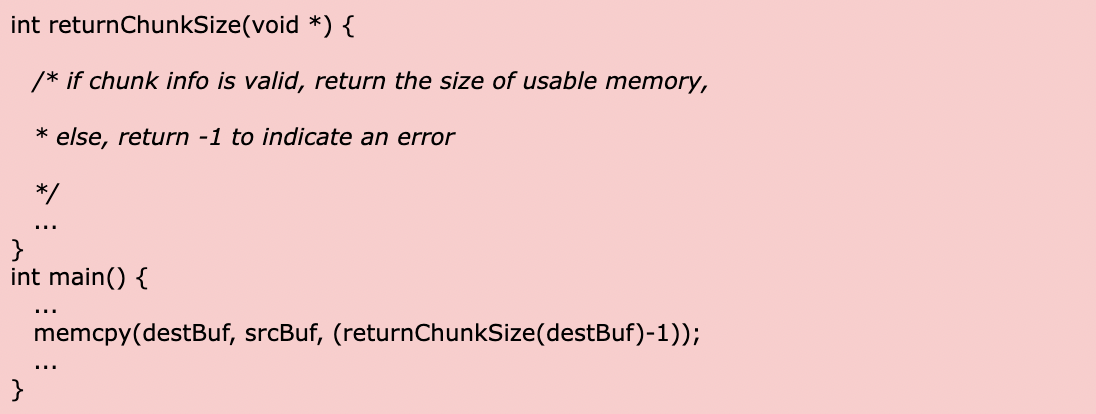
This weakness can cause programs to overwrite important information or even overwrite data belonging to other program parts. It can also cause software crashes and open up vulnerabilities that attackers can exploit.
By understanding how CVE and CWE work, developers can take extra measures to create more secure software.
CVE and CWE FAQs
Still have questions about CVE and CWE? Here are frequently asked questions about these two cybersecurity concepts.
How are CVEs found?
Anyone can discover and report a CVE, including organizations, security researchers, and users. Companies like Microsoft also offer bug bounty programs to incentivize individuals to report software bugs.
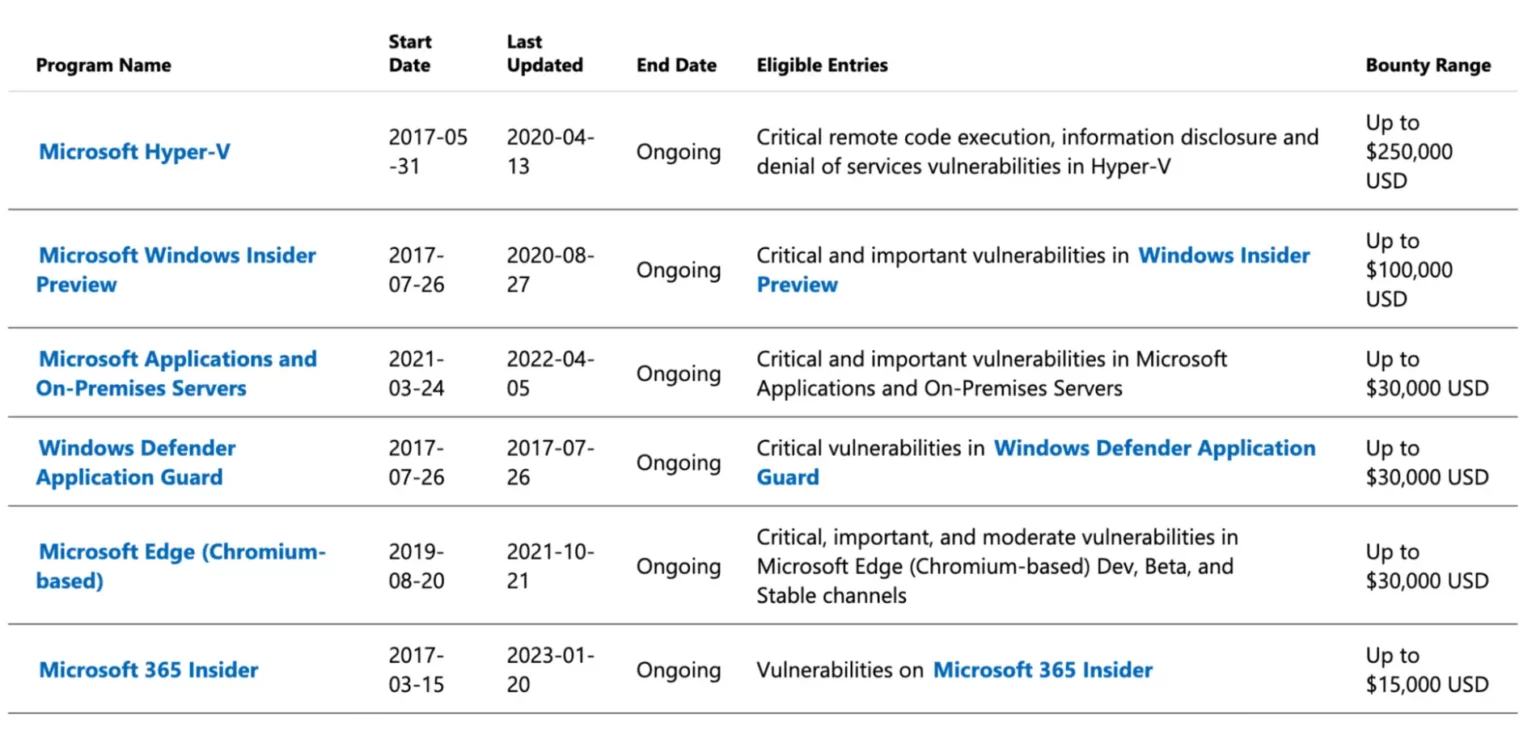
New vulnerabilities are reported to the CVE Program. If a vulnerability meets certain criteria, it receives a new CVE Identifier (CVE ID) and gets published in the CVE database. Sometimes, the publication of a new CVE may be delayed to give vendors time to patch it.
How can developers use CVE and CWE?
Developers can use CVE and CWE to make software products more secure. For example, a developer can search the CVE list to identify known vulnerabilities in the software they’re working with. They can also use the scoring systems that CVE and CWE use to assess and prioritize software issues.
What is the CWE Top 25?
The CWE top 25 lists the top 25 most dangerous software weaknesses. These include out-of-bounds writing, cross-site scripting, and SQL injections.
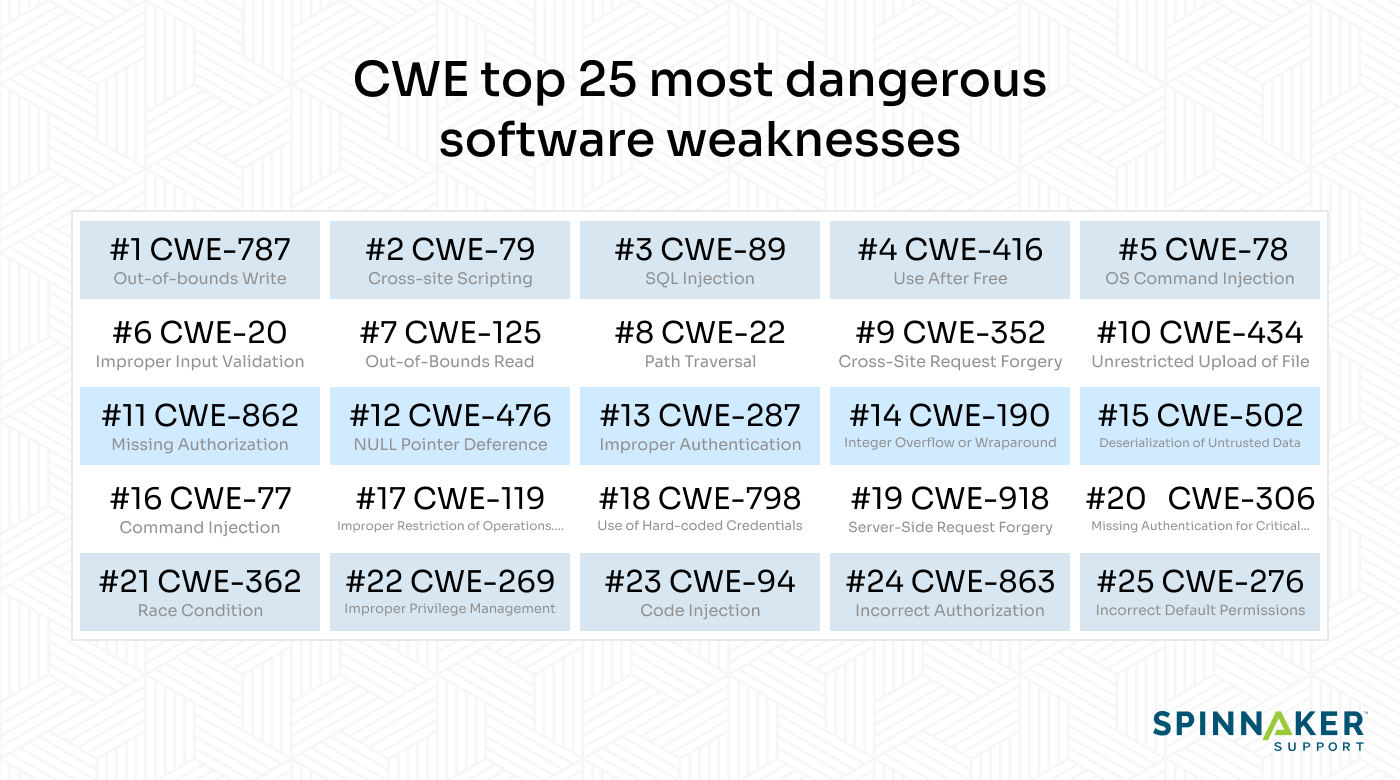
Learning about these weaknesses can help developers improve the safety of their software.
How do you detect software vulnerabilities in code?
Developers and security professionals use different methods to detect software vulnerabilities. These include:
- Static code analysis: A method of debugging an application’s source code without executing it. This helps identify vulnerabilities early in the software development process.
- Dynamic Application Security Testing (DAST): A method of testing an application while it’s running in a live environment. DAST tools can run security scans and find potential flaws attackers can exploit, like SQL injections.
- Manual code review: A manual review of an application’s source code line by line to identify vulnerabilities and logic flaws that automated tools may miss.
How do you fix critical CVEs?
Software vendors typically release security advisories that detail a vulnerability and include instructions on addressing it. If you’re running software with a known vulnerability, visit the vendor’s website and search for an update that addresses the CVE. Then, download and apply the patch. Be sure to follow the instructions to ensure proper installation carefully.
CVE case study: How Spinnaker Support handles software vulnerabilities
The Log4j or “Log4Shell” vulnerability (CVE-2021-44228) made headlines when first published in the National Vulnerability Database in December 2021. It allowed attackers to take control of unpatched Java-based systems via remote code execution.
New security vulnerabilities are always cropping up, of course, but Log4j was especially concerning because it affected enterprise applications including Oracle, SAP, and IBM, and it left hundreds of millions of devices vulnerable to malicious scripts.
Jen Easterly, director of the US Cybersecurity and Infrastructure Security Agency (CISA), said Log4j “is one of the most serious I’ve seen in my entire career, if not the most serious.”
Fixing vulnerabilities isn’t always as straightforward as installing a patch. Enterprise software often has custom configurations that may not be compatible with an update. Complicating matters further is that software vendors typically don’t support custom code.
So, how did our team respond?
When the Log4j vulnerability was published, our experts got to work on analyzing it. Our client’s IT infrastructure insights allowed us to develop remediation measures. We advised our clients to locate the affected library and patch it with the correct version.
Here’s a timeline of how our experts addressed the Log4j vulnerability:
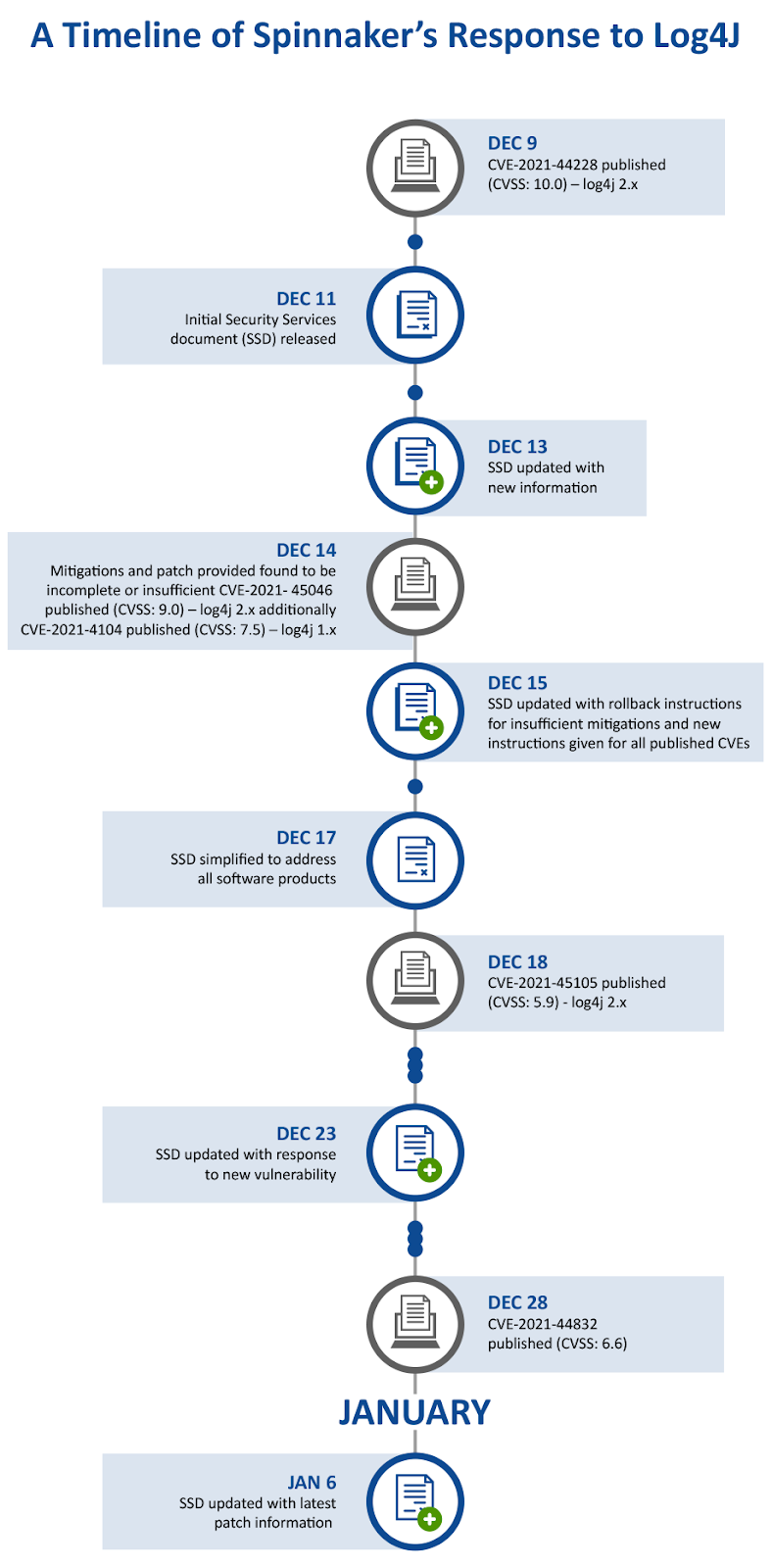
Our response to the Log4j vulnerability demonstrates our customer-first approach to security.
CVE-2021-44228 was an exceptional situation, earning a CVSS score of 10.0. Instead of targeting individual CVEs, we follow an in-depth approach to security that involves helping companies implement full-scale defense strategies to reduce vulnerabilities.
Improve your security posture with Spinnaker Shield
CVE and CWE play vital roles in cybersecurity. Developers can use them to improve code quality, prioritize vulnerabilities, and deliver more secure software.
Staying on top of your company’s security posture isn’t easy. Attackers are continuously on the lookout for new vulnerabilities they can exploit.
We offer comprehensive security solutions for enterprise software like Oracle, SAP, and JD Edwards. Spinnaker Shield takes a proactive approach to risk mitigation. Our experts design an extensive defense strategy that’s tailored to your IT infrastructure.
Contact us today to learn how our Defense in Depth system can improve your security posture and mitigate risks across your systems.


