Author – Tim Boles, Director, Security Solutions
It starts with a patch, right? We have all seen the reports from DHS (Department of Homeland Security) and CISA (Cybersecurity & Infrastructure Security Agency) around the importance of patching. Typically, it almost always begins with:
Step 1 = Patch your system now!
Step 2 = Patch Management
Patching has been around for over 20 years, and there are still critical issues. However, as of 2022, we are seeing organizations take up to 60 days, on average, to patch critical risk vulnerabilities, and of the vulnerabilities covered under patch management, only 10% of known vulnerabilities are addressed with each patch. It is quite a bit of risk for an organization, leaving systems vulnerable for up to two months, and once the fix comes in, it probably won’t even address most of the CVEs (Common Vulnerabilities and Exposures). Luckily, security doesn’t have one correct answer, and we can find the solution through various paths.
What is Security Patching?
Security Patching allows code changes to designed software to help eliminate bugs, fix vulnerabilities, and improve performance. The industry average for code defects is 15-50 errors per 1000 lines of delivered code. Depending on the software publisher, security patches can be part of your service package, added a la carte, or provided to the end user at no cost.
In 2021, 20,194 security vulnerabilities (CVEs) were published, an increase from 17,055 in 2020. It can feel a bit overwhelming trying to keep up with all the patches as the vulnerabilities are only growing, but the shortcomings go beyond simply the management:
• Patching takes time and won’t be available for months after the initial vulnerability is identified
• Patches are unable to combat zero-day vulnerabilities
• Patches require testing both during production and deployment
• Patches are not developed for older product versions and applications
• Patches are one-size-fits-all, and software ecosystems are complex and unique environments
• Many organizations are unable to patch regularly due to operational constraints
Businesses are realizing the pitfalls of this model and are beginning to implement other risk mitigation tactics to keep their organizations safe.
Seven-Point Security
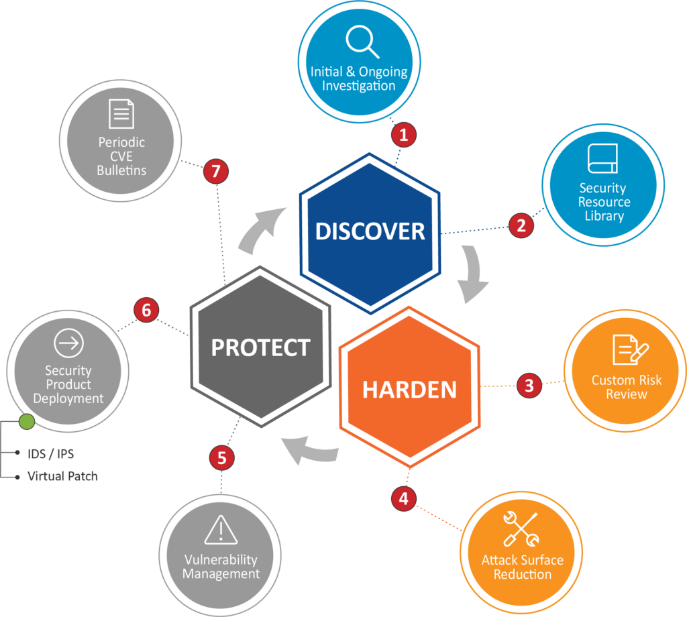
Spinnaker Support addresses the concerns around vulnerabilities with a Seven-Point Security Solution standard for all support customers and exceeds the performance of patches alone as a CVE solution. From Day 1, our team works with you through the processes around the solution with the core concepts of discover, harden, and protect for your data and critical systems. This technique allows resolutions of issues as they occur rather than a couple months later and puts the necessary controls and tools in place to maintain a secure environment.
This refined approach begins with an initial risk assessment and ends with continuous IT Security vulnerability management. Throughout this process, we will deploy the multiple services which make up Seven-Point Security:
1. Initial and Ongoing Investigation
2. Security Resource Library
3. Custom Risk Review
4. Attack Surface Reduction
5. Vulnerability Management
6. Security Product Deployment
7. Periodic CVE Bulletins
Proper security is a process, not a patch, and requires a vast Defense in Depth strategy to protect your organization against potential threat actors.
Going Beyond the Patch
Vulnerabilities and exposures are happening exponentially, and it is becoming more challenging to keep up with them simply by patching. A holistic security posture will help your organization be proactive in security threats and allow for streamlined risk mitigation.
We invest in your security and compliance measures with the same exacting standards we apply to our organization. Our security solutions are designed for your unique set of applications and systems. It combines proven processes and experienced staff to continuously investigate issues, harden and protect your environment, and deliver timely fixes and remediations.
Security can be a cumbersome topic, but we are here to help. If you have questions about how our Seven-Point Security Solution works, please get in touch with us today.
For more information, please visit
https://www.spinnakersupport.com/third-party-support/security-vulnerability/


